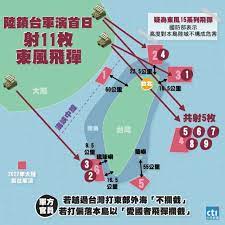
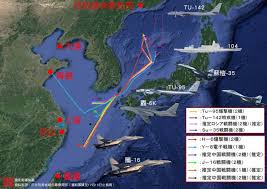
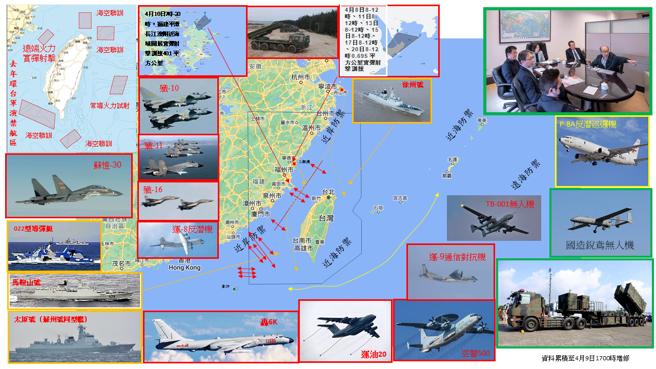
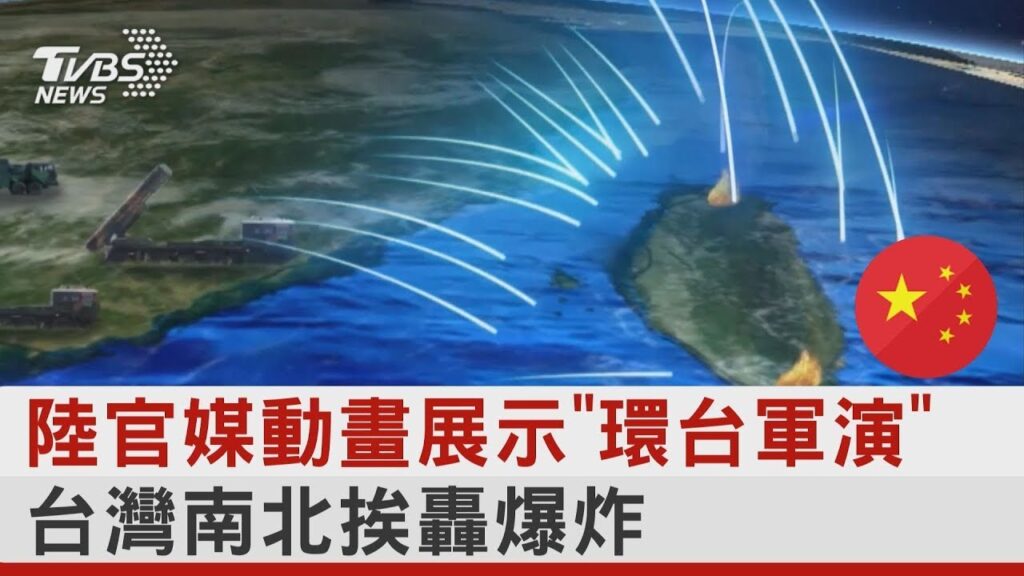
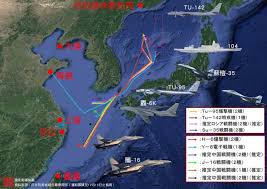
中國軍事-以認知為中心的戰爭:因應複雜戰爭的作戰理念
音譯外語:
Complexity science is one of the frontier fields of contemporary scientific development. It is a new tool for understanding, understanding, and exploring the phenomena, laws, and mechanisms of war. As the form of war evolves from information war to intelligent war, the complexity of war shows an exponential growth trend, and it becomes increasingly difficult to seize control of information. The key to combat is to put the enemy into a “decision-making dilemma” so that it can even Even with information superiority, it cannot make correct decisions, thus losing its combat advantage. The focus of operations will change from “information-centered” to “cognition-centered”, and the winning mechanism will change from “information winning” to “cognitive winning”.
“Three changes” reveal the driving forces behind the increasing complexity of war
War is a field full of possibilities, and change is the basic characteristic that runs through it. President Xi stressed that we must pay close attention to changes in technology, war, and opponents. Changes in science and technology are the foundation, changes in war are the subject, and changes in opponents are the key. Changes in science and technology lead to changes in war, and changes in war prompt changes in opponents. The “three changes” have promoted the evolution of war forms, the expansion of war fields, the transformation of war goals, and the expansion of war influence, revealing the driving forces behind the growth of war complexity.
Changes in technology have overturned the basis for winning wars. Science and technology are the core combat effectiveness and the most active and revolutionary factor in military development. Throughout the history of the world’s military development, every major scientific and technological innovation has started a new military revolution, and every military revolution has pushed military development into a new era. Scientific and technological innovation has become a huge engine to improve the military’s combat effectiveness. . At present, a new round of scientific and technological revolution and military revolution are accelerating. The degree of informatization of modern warfare is constantly increasing, and the characteristics of intelligence are becoming increasingly apparent. The role of driving the military revolution is becoming more and more prominent. The rapid development of some cutting-edge technologies may fundamentally change the face of war and war. According to the rules, the military game between great powers is more embodied in technological subversion and counter-subversion, raids and counter-raids, offsets and counter-offsets. The U.S. Navy’s “Nemesis” project includes reconnaissance, decoy, jamming and other systems. The decoy system covers air, surface and underwater. Under the scheduling and control of the distributed artificial intelligence engine, it can complement each other, coordinate deception, and truly create a A “ghost aircraft carrier formation” completely subverted traditional electronic deception methods and raised information deception to an unprecedented level. It can be said that science and technology has never had such a profound impact on the overall situation of national security and military strategy as it does today. It has profoundly intervened in, supported, and dominated the evolution of war forms and the innovation of combat styles, and has even subverted the mechanism of winning wars.
The U.S. Navy’s “Nemesis” project is based on networked collaborative electronic warfare
Concept, integrating different systems and utilizing unmanned distributed
Clusters of electronic warfare platforms enable large-scale collaborative electronic warfare
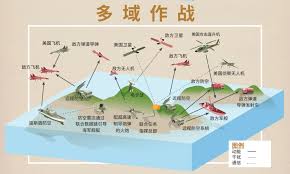
The changes in war highlight the complexity of war. Modern warfare is undergoing profound changes, showing unprecedented diversity and complexity. This super complexity stems from many reasons: first, various advanced technologies or weapons are constantly emerging, bringing many uncertainties; second, the battlefield covers land, sea, air, space, network, electricity and cognitive and other multiple third, multiple combat objects, combat styles, combat areas, and combat methods are cross-correlated and combined to form a complex “hybrid war”; fourth, artificial intelligence algorithms build a large number of combat elements into a complex logic, and use human Machine speed beyond the reach of thinking prompts the combination, deconstruction, and recombination of various elements. In the Ukraine crisis in 2022, on the surface it is a confrontation between Russia and Ukraine, but in essence it is a “hybrid war” between the United States and Western countries and Russia; the Russian and Ukrainian armies extensively use military and civilian drones to expand The “unmanned +” application model shows the prototype of future unmanned intelligent operations; with the support of U.S. NATO air and space situational intelligence, the Ukrainian army frequently uses low-cost unmanned equipment to carry out raids on important Russian weapons platforms, highlighting its new qualities Combat forces have asymmetric attack advantages against large weapons and equipment in traditional combat systems. Changes in technology will eventually lead to changes in war. The impact of a single element on war will become weaker and weaker. The joint combat system composed of multiple elements will have a complex impact on war. War is non-linear, uncertain, chaotic and open. Complex characteristics such as adaptability and confrontation will increase exponentially, which will make it more difficult for people to judge the progress and outcome of the war.
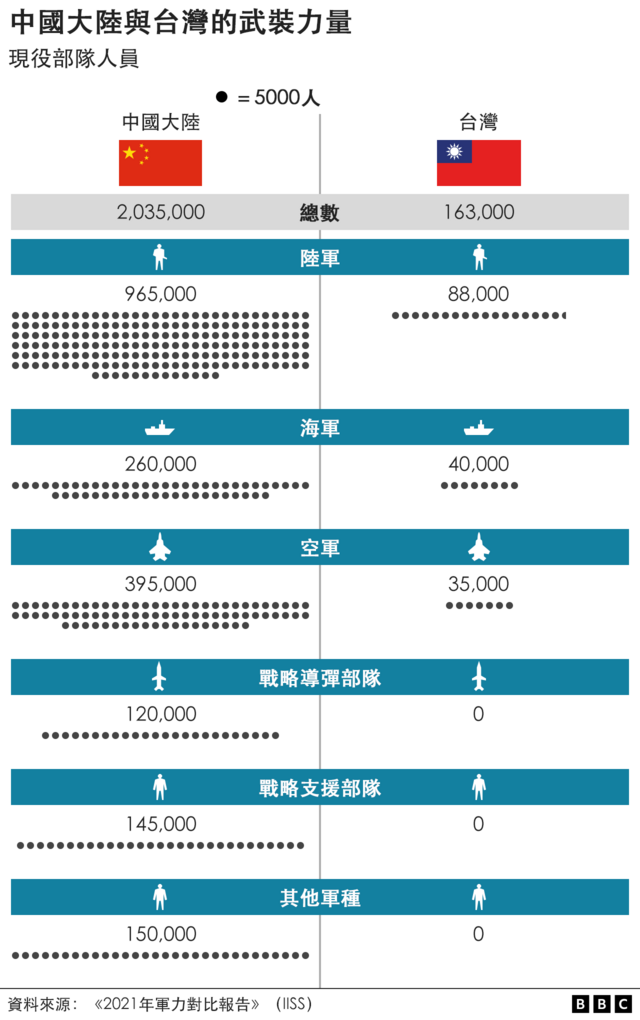
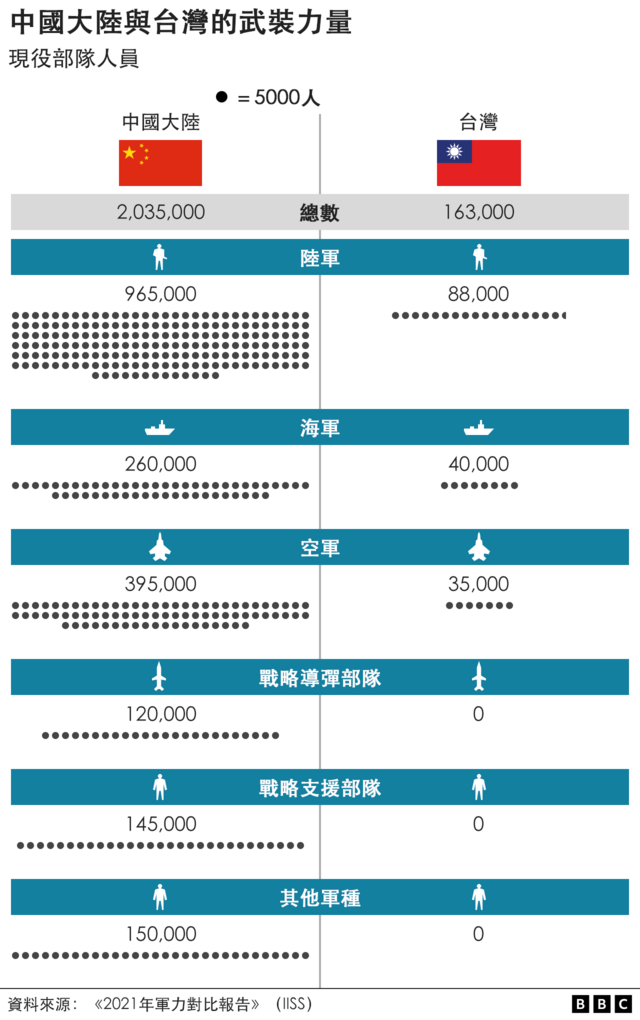
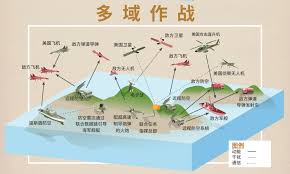
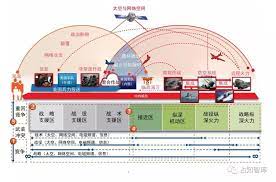
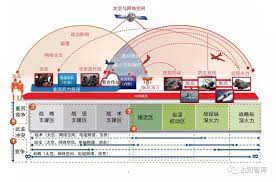
Changes in opponents accelerate the growth of war complexity. Changes in war prompt changes in opponents. Currently, we are experiencing major changes unseen in a century. Major military powers are actively making strategic adjustments and promoting a new round of military reforms, which exhibit the following characteristics: first, the trend of joint, miniaturized, and autonomous institutional establishments has become more obvious; second, The first is that weapons and equipment are showing a development trend of digitization, precision, stealth, unmanned, and intelligence; the third is that the combat form is moving towards the “four nons” (non-contact, non-linear, asymmetric and irregular) and the “three nos” (Invisible, silent, unmanned) combat; fourth, the military command form is developing in the direction of flattening, automation, networking, and seamlessness. The United States regards China as its main strategic opponent and strives to suppress and contain China. It has vigorously strengthened the innovation of operational concepts and has successively proposed new operational concepts such as “hybrid warfare”, “multi-domain warfare” and “mosaic warfare”, claiming that it will fight to defeat its opponents. A high-end war in which “technology cannot be understood, strikes are difficult to predict, and speed cannot keep up.” The core of the US military’s “mosaic warfare” is unmanned, low-cost, fast, lethal, flexible and reconfigurable. It is based on distributed situational awareness, with the help of intelligent auxiliary decision-making tools and the concept of building blocks and jigsaw puzzles to adaptively formulate mission planning. , dynamically reorganize combat forces, decompose the functions of the combat platform into a larger number of single-function nodes, and build a combat system with a large number of functional nodes. Replace the “kill chain” with a “kill network”. Several nodes will fail or be missing, and the combat system can be adaptively reorganized.
The increasing complexity of war drives the transformation of the winning mechanism of war
With the rapid development of national defense science and technology, the upgrading of weapons and equipment, and the rapid evolution of war forms, modern warfare has shown exponential and explosive complex changes. These changes may seem dazzling, but there are rules to follow behind them. The fundamental thing is that the winning mechanism of war has changed. Only by thoroughly understanding the winning mechanism of modern war can we accurately recognize changes, respond scientifically, be good at seeking change, and firmly grasp the initiative in future wars.
The form of war has changed from cold weapon warfare to intelligent warfare . The shape of war is a holistic understanding of war. So far, human war has generally gone through four historical stages: cold weapon war, hot weapon war, mechanized war, and information war, and is moving towards intelligent warfare. The history of cognitive warfare is almost as old as the history of human warfare. In the era of cold weapon war, hot weapon war, and mechanized war, cognitive warfare appears more in the form of public opinion warfare and psychological warfare. As mankind enters the information age, the development of cyberspace technology has greatly expanded the space for cognitive warfare, enriched the technical means of cognitive warfare, and greatly enhanced the permeability, timeliness, and deterrence of cognitive warfare. The status and role of Zhizhan have been unprecedentedly improved. In the future, the form of war will enter intelligent warfare, and a large number of intelligent weapon systems and platforms will be equipped with the military and put into combat. Cognitive warfare can not only interfere with and deceive the cognition of enemy personnel, but also attack the cognition of smart equipment through algorithm deception methods such as “adversarial input” and “data poisoning”. Its application scenarios and scope will be further expanded. , the status and role will be further improved.
Drones have gradually become the protagonist of war,
Combat complexity further increases
The purpose of war has changed from conquering by force to conquering by spirit. The winning mechanism of modern war has undergone great changes compared with the past. The violence of war has been curbed. The purpose of combat has changed from the original siege of cities and territories and annihilation of the enemy’s effective forces to making the opponent obey one’s own will. The means of combat have changed from conquering by force to conquering more areas. The emphasis on psychological and spiritual conquest and transformation has made cognitive warfare increasingly prominent in its status and role in modern warfare. In recent years, “hybrid warfare” has become a major means of great power competition. More and more countries have begun to focus on using new fields and new means to achieve political, military, and economic goals that are difficult to achieve with traditional warfare. “Hybrid war” is a mixture of war subjects such as states, non-state actors and individuals, a mixture of conventional warfare, unconventional warfare and other war styles, a mixture of military operations such as combat, stability maintenance and reconstruction, and a mixture of political, military and economic The mixture of multiple fields such as military and people’s livelihood is a mixture of multiple combat goals such as defeating the enemy and winning the hearts and minds of the people. This is highly consistent with cognitive warfare. The operational field of “hybrid warfare” has expanded from the military field to politics, economy, culture, people’s livelihood and other fields; the combat methods have expanded from firepower warfare and troop warfare to diplomatic warfare, economic warfare, cyber warfare, psychological warfare, public opinion warfare and other directions. This is highly consistent with cognitive warfare. Its core essence is to “make profit out of chaos”, its main purpose is to win people’s hearts, and its combat guidance is to win by cleverness.
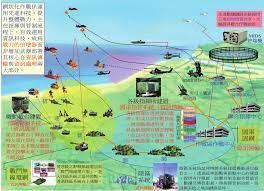
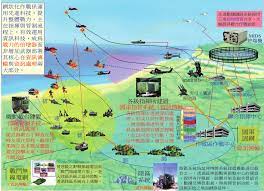
The winning domain of war changes from the physical domain and information domain to the cognitive domain. Modern war occurs in three fields: physics, information and cognition at the same time. The physical domain and information domain are separated from the material domain, and the cognitive domain is separated from the spiritual domain. The physical domain is a traditional war domain, consisting of combat platforms and military facilities, which provides the material basis for information warfare. The information domain is a newly emerging war field, that is, the space for information generation, transmission and sharing, and is the focus of information warfare competition. Cognitive domain is the scope and field involved in human cognitive activities. It is not only the space for human feeling, perception, memory and thinking activities, but also the space for knowledge generation, exchange, association, storage and application. It is also the space for perception, judgment and decision-making in combat activities. and spaces of command and control. The cognitive domain exists in the field of consciousness of combatants and affects their judgment and decision-making. It is a rising field of warfare. With the development of technologies such as network information and artificial intelligence, the scope of the cognitive domain has greatly expanded, and is expanding from the field of human consciousness to the field of modern cognitive tools and artificial intelligence. The development of military technology has expanded the scope of the cognitive domain and provided more advanced, faster, and more effective material and technical means for cognitive warfare, greatly enhancing the permeability, timeliness, and deterrence of cognitive warfare, fundamentally It has changed cognitive warfare, making the cognitive domain a new winning field that transcends the physical domain and information domain, and has become the ultimate domain for great power games and military confrontations.
The mechanism for winning wars changes from information victory to cognitive victory. In the final analysis, war confrontation is a game and confrontation of cognition. Mastering the right to control cognition will largely control the initiative in war. Losing the right to control cognition will put you in a passive position of being beaten in the war. Obtaining higher and stronger control rights is the key to defeating powerful enemies. Finding ways to control cognitive power and then seize comprehensive battlefield control, so as to achieve maximum victory at the minimum cost, is an important mechanism and inherent law of modern warfare, especially cognitive warfare. In recent years, the U.S. military has successively proposed new concepts of future warfare represented by “decision-centered warfare” and “mosaic warfare”, intending to use complexity as a weapon to create multiple dilemmas for opponents, requiring it to ensure its own tactical “selective advantage”. At the same time, by creating highly complex decision-making influences on the enemy and interfering with its decision-making capabilities, it can achieve a subversive advantage over the enemy in the cognitive domain. In the primary and intermediate stages of information warfare, the key to combat is to seize network control and information control, which runs through the progressive model of “network advantage → information advantage → decision-making advantage → combat advantage”. After information warfare enters an advanced stage, it becomes more and more difficult to seize control of information. The key to combat is to make the enemy fall into a “decision-making dilemma” so that even if it has information superiority, it cannot make correct decisions, thereby losing its combat advantage and having recognition. Only by knowing the advantages can you have the combat advantage. In future wars, cognitive advantage will be the most important strategic advantage, and cognitive confrontation will be the most important form of confrontation. It can be said that “without cognition, there is no war.”
Coping with complex wars has given rise to the concept of cognitive-centered warfare
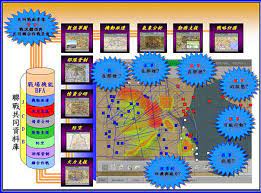
In order to cope with the exponential growth trend of the complexity characteristics of modern warfare, we must use the theories and methods of complexity science to change the concept of platform-centered warfare where firepower is supreme and killing is king, and establish a cognitive-centered combat thinking. Cognition-centered warfare refers to taking the cognitive domain as the winning area, taking the cognitive advantage as the operational goal, and focusing on interfering with cognitive means, suppressing cognitive channels, affecting cognitive production, and conducting cognitive operations on enemy personnel and intelligent equipment. Interference, suppression, deception and inducement are a new operational concept that obtains combat advantages by seizing and maintaining cognitive advantages. Its main winning mechanisms are as follows.
Sun Tzu mentioned in “The Art of War” that “there is no constant force in an army;
Water has no permanent shape; those who can win due to the changes of the enemy are called gods.
Use cyber deterrence to destroy the enemy’s will to fight. Targeting the enemy’s political, economic, military, diplomatic, and cultural contradictions and weaknesses, disseminate deterrent information through cyberspace, or publish military parades, large-scale military exercises, new weapons and equipment research and development and other information through the Internet, so as to cause extreme cognitive and psychological changes in the opponent. Great fear and shock, deterring the enemy is not conducive to the implementation of my actions. Comprehensive use of network and electricity attack methods to carry out point strikes and warning attacks against the enemy’s important network and electricity targets and key core nodes, destroying the enemy’s system combat capabilities, affecting the normal performance of the enemy’s weapons and equipment, and providing psychological deterrence to the enemy. The US military’s “gray zone operations” theory relies on its own technological advantages and mainly takes actions such as cyber and electronic countermeasures to respond to the opponent’s “gray zone provocation” and deter the opponent from giving up “confrontation” or escalating the conflict, putting it in a dilemma.
Use information deception to induce the enemy to make misjudgments. Aiming at the enemy’s reconnaissance equipment, intelligence agencies and command systems, use cyber attacks, electronic deception and other means to conceal one’s military intentions, military operations and military objectives, and transmit to the enemy erroneous and false combat plans, troop configurations and operations. capabilities, combat plans, battlefield situation, etc., or use the enemy’s command information system to send false orders and information to induce the enemy to make wrong judgments and disrupt the enemy’s combat command. Implement new attacks such as “adversarial input” and “data poisoning” against artificial intelligence algorithms, allowing them to obtain preset conclusions through deep learning training, or causing them to fall into local optimal solutions and ignore the global optimal. Use technologies such as computer imaging, video synthesis, virtual reality, and artificial intelligence to synthesize sound, video, images, text information, etc., or use “deep fake” technology to generate false information that is confusingly real and difficult to distinguish between true and false, and transmit it through the Internet Spread in large quantities to confuse and deceive opponents and influence their decisions and actions.
Use information suppression to block the enemy’s cognitive means. Target the enemy’s important network targets, as well as core routers, switches, gateways, key servers, etc., and use “soft” and “hard” attack methods to destroy their network nodes. Based on the networking characteristics of wireless links such as the enemy’s command and control network, communication transmission network, weapon hinge network, and early warning detection network, comprehensively use technologies and means such as electronic jamming, GPS spoofing attacks, command link takeover, and data hijacking control to suppress them. data communication, blocking its communication links and interfering with its combat command. Implement cyber-paralysis attacks on enemy command and control, military communications, early warning detection, aerospace information and other military networks, destroying core networks that affect their operations and weakening their combat capabilities.
Use public opinion propaganda to create a favorable public opinion environment . Cooperate with the country’s political, military, and diplomatic struggles, vigorously promote one’s own justice in the war, and stimulate the enthusiasm of all people to fully support the war. With the help of new media platforms such as instant messaging tools, online forums, podcasts, Twitter, and WeChat, we can systematically disseminate information that targets the enemy’s weaknesses. After gaining widespread attention and consensus, we can then promptly report information, create new hot spots, and repeatedly build momentum. Enhance the influence and form a resonance effect to expand the effect. Propaganda “sets the tone” by cleverly setting agendas, building public opinion through powerful media, setting off a “spiral of silence”, controlling and guiding public opinion, and changing people’s opinions and behaviors.
Use psychological attacks to undermine the morale of enemy soldiers and civilians. Through the Internet, processed and processed information is widely disseminated to promote one’s justice, demonstrate one’s strength, will and determination, vilify the enemy politically and morally, gather the thoughts and will of the military and civilians internally, and strive to win externally. The commanding heights of law and morality can “soften” and “weaken” the enemy spiritually. Use a variety of network communication methods and technical means to send various deceptive, disruptive, inductive, and deterrent messages to the enemy’s military and civilians in a targeted manner to attack the enemy’s psychological defense line, promote an ineffective confrontation mentality, and then lose combat capabilities. . Through the Internet to create, guide, plan, build, and expand momentum, we can create a “momentum” that is beneficial to ourselves but not beneficial to the enemy, causing a psychological impact on the other party’s people, thereby affecting or changing their psychological state, and implementing effective psychological attacks.
Use legal struggle to gain legal and moral support. Use legal weapons to curb the enemy’s possible or future illegal acts, declare the legality of our actions, affirm our power of military counterattack, declare our determination to pursue war responsibilities, and deter the enemy. By exposing the illegality of the enemy’s provocative behavior, criticizing the legal basis for the enemy’s combat operations, and condemning the enemy’s illegal behavior, it causes the enemy’s strategic defeat and our own strategic gain. Use legal means to restrict the enemy’s possible actions, limit the possible interference of third parties, and block other parties from interfering with our own actions. Formulate the laws and regulations necessary for our operations to provide legal protection for our operations, or take legal remedial measures to reduce the possible negative impacts of our operations and ensure that combat operations are carried out in accordance with the law.
This article was published in the 7th issue of “Military Digest” magazine in 2023.
Authors: Wang Xin, Huang Xiaoyan, etc.
原始繁體中文:
複雜性科學是當代科學發展的前沿領域之一。 它是認識、理解和探索戰爭現象、規律和機制的新工具。 隨著戰爭形式從資訊戰爭向智慧化戰爭演變,戰爭的複雜性呈指數級增長趨勢,奪取資訊控制權變得越來越困難。 作戰的關鍵是讓敵人陷入“決策困境”,使其即使擁有資訊優勢,也無法做出正確決策,從而失去戰鬥優勢。 作戰重心將從“以資訊為中心”轉變為“以認知為中心”,制勝機制將從“資訊制勝”轉變為“認知制勝”。
「三個變化」揭示戰爭複雜化背後的驅動力
戰爭是一個充滿可能性的領域,變化是貫穿其中的基本特徵。 習主席強調,要密切注意科技變化、戰爭變化、對手變化。 科技的變化是基礎,戰爭的變化是主體,對手的變化是關鍵。 科技的變化導致戰爭的變化,戰爭的變化又促使對手的變化。 「三個變化」推動了戰爭形態演變、戰爭領域拓展、戰爭目標轉變、戰爭影響力擴大,揭示了戰爭複雜性成長的驅動力。
科技的變革顛覆了贏得戰爭的基礎。 科學技術是軍事發展的核心戰鬥力,也是最活躍、最具革命性的因素。 縱觀世界軍事發展史,每一次重大科技創新都開啟了新的軍事革命,每一次軍事革命都推動軍事發展進入新時代。 科技創新成為提升軍隊戰力的巨大引擎。 。 目前,新一輪科技革命和軍事革命正在加速推進。 現代戰爭資訊化程度不斷提高,智能化特徵日益顯現。 推動軍事革命的角色日益凸顯。 一些尖端技術的快速發展可能會從根本上改變戰爭和戰爭的面貌。 依照規則,大國之間的軍事博弈更體現為技術顛覆與反顛覆、突襲與反突襲、抵銷與反抵銷。 美國海軍的「復仇女神」計畫包括偵察、誘餌、幹擾等系統。 誘餌系統覆蓋空中、水面和水下。 在分散式人工智慧引擎的調度和控制下,可以優勢互補,協同欺騙,真正打造出「幽靈航空母艦編隊」,徹底顛覆傳統電子欺騙手段,將資訊欺騙提升到前所未有的水平。 可以說,科學技術從來沒有像今天這樣對國家安全和軍事戰略大局產生如此深刻的影響。 它深刻地介入、支持、主導戰爭形態的演變和作戰方式的創新,甚至顛覆了戰爭的勝利機制。
美國海軍「復仇女神」計畫基於網路化協同電子戰
概念,整合不同系統並利用無人分散式
電子戰平台集群可實現大規模協同電子戰
戰爭的變化凸顯了戰爭的複雜性。 現代戰爭正在發生深刻變化,呈現前所未有的多樣性和複雜性。 這種超級複雜性源自於多種原因:一是各種先進技術或武器不斷湧現,帶來許多不確定性; 第二,戰場涵蓋陸、海、空、天、網、電、認知等多個 第三,多種作戰對象、作戰方式、作戰領域、作戰方式相互關聯、組合,形成複雜的“混合戰爭” ; 第四,人工智慧演算法將大量的戰鬥元素建構成複雜的邏輯,並以人類思維無法企及的速度提示各種元素的組合、解構、重新組合。 2022年的烏克蘭危機,表面上是俄羅斯與烏克蘭的對抗,實質上是美國與西方國家與俄羅斯的「混合戰爭」; 俄羅斯和烏克蘭軍隊廣泛使用軍用和民用無人機,拓展「無人+」應用模式,展示了未來無人智慧作戰的雛形; 在美國北約空天態勢情報支援下,烏克蘭軍隊頻繁使用低成本無人裝備對俄羅斯重要武器平台實施突襲,凸顯其新素質 作戰部隊在傳統作戰中對大型武器裝備具有非對稱攻擊優勢系統。 科技的變革最終會導致戰爭的變革。 單一因素對戰爭的影響會越來越弱。 由多種要素組成的聯合作戰體系將對戰爭產生複雜的影響。 戰爭是非線性的、不確定的、混亂的和開放的。 適應性、對抗性等複雜特徵將呈指數級增長,這將使人們更難以判斷戰爭的進展和結果。
對手的變化加速了戰爭複雜性的成長。 戰爭的變化促使對手的變化。 目前,我們正面臨百年未有之大變局。 主要軍事強國正積極進行戰略調整,推動新一輪軍事改革,呈現以下特徵:一是機構設置聯合化、小型化、自主化趨勢更加明顯。 二是一是武器裝備呈現數位化、精確化、隱身化、無人化、智慧化發展趨勢; 第三是作戰形式正在走向「四非」(非接觸、非線性、不對稱、不規則)和「三無」(隱形、無聲、無人)作戰; 第四,軍事指揮形態朝向扁平化、自動化、網路化、無縫化方向發展。 美國將中國視為主要戰略對手,極力打壓和遏制中國。 它大力加強作戰理念創新,先後提出「混合戰」、「多域戰」、「馬賽克戰」等新作戰概念,號稱要打贏對手。 一場「技術看不懂、打擊難以預測、速度跟不上」的高端戰爭。 美軍「馬賽克戰」的核心是無人、低成本、快速、致命、靈活、可重構。 它基於分佈式態勢感知,借助智慧輔助決策工具以及積木和拼圖的概念,自適應地制定任務規劃。 ,動態重組作戰力量,將作戰平台的功能分解為數量較多的單一功能節點,建構具有大量功能節點的作戰系統。 將「殺傷鏈」替換為「殺傷網」。 多個節點會發生故障或遺失,戰鬥系統可以自適應重組。
戰爭日益複雜,驅動戰爭制勝機制轉變
隨著國防科技的快速發展、武器裝備的更新換代、戰爭形態的快速演變,現代戰爭呈現指數級、爆炸性的複雜變化。 這些變化看似令人眼花撩亂,但背後卻有規則可循。 根本的是戰爭的勝利機制發生了變化。 只有深刻認識現代戰爭的勝利機制,才能準確認識變化、科學應對、善於求變,牢牢掌握未來戰爭主動權。
戰爭形式已從冷兵器戰爭轉變為智慧戰爭。 戰爭的形狀是灑紅節迄今為止,人類戰爭大致經歷了冷兵器戰爭、熱兵器戰爭、機械化戰爭、資訊戰爭四個歷史階段,並且正走向智慧化戰爭。 認知戰爭的歷史幾乎與人類戰爭的歷史一樣悠久。 在冷兵器戰爭、熱兵器戰爭、機械化戰爭時代,認知戰更以輿論戰、心理戰的形式出現。 隨著人類進入資訊時代,網路空間科技的發展極大拓展了認知戰的空間,豐富了認知戰的技術手段,大大增強了認知戰的滲透性、時效性、威懾力。 知展的地位和作用得到空前提升。 未來戰爭形態將進入智慧化戰爭,大量智慧武器系統和平台將裝備軍隊並投入戰鬥。 認知戰不僅可以乾擾和欺騙敵方人員的認知,還可以透過「對抗性輸入」、「資料投毒」等演算法欺騙手段攻擊智慧裝備的認知。 其應用場景和範圍將進一步擴大。 ,地位和作用將進一步提高。
無人機逐漸成為戰爭的主角,
戰鬥複雜性進一步增加
戰爭的目的已經從武力征服轉變為精神征服。 現代戰爭的勝利機制與過去相比發生了很大的變化。 戰爭的暴力已經被遏止。 作戰目的由原來的圍攻城市和領土、殲滅敵人有生力量轉變為使對手服從自己的意志。 作戰手段由武力征服轉變為征服更多地區。 對心理精神征服與改造的重視,使得認知戰在現代戰爭中的地位與角色日益凸顯。 近年來,「混合戰爭」成為大國競爭的主要手段。 越來越多的國家開始專注於利用新領域、新手段來實現傳統戰爭難以實現的政治、軍事、經濟目標。 「混合戰爭」是國家、非國家行為體和個人等戰爭主體的混合,是常規戰爭、非常規戰爭等戰爭方式的混合,是作戰、維穩、重建等軍事行動的混合,是軍事行動的混合。政治、軍事、經濟的混合軍事、民生等多個領域的混合,是戰勝敵人、贏得民心等多重作戰目標的混合。 這與認知戰高度一致。 「混合戰爭」的作戰領域從軍事領域擴展到政治、經濟、文化、民生等領域; 作戰方式從火力戰、兵力戰拓展到外交戰、經濟戰、網路戰、心理戰、輿論戰等方向。 這與認知戰高度一致。 其核心本質是“亂中取利”,其主要目的是贏得人心,其作戰指導是以智取勝。
戰爭的勝利領域從物理領域、資訊領域轉向認知領域。 現代戰爭同時發生在物理、資訊和認知三個領域。 物理領域和資訊領域與物質領域分離,認知領域與精神領域分離。 物理域是傳統的戰爭域,由作戰平台和軍事設施組成,為資訊化戰爭提供物質基礎。 資訊域是一個新興的戰爭領域,即資訊產生、傳輸和分享的空間,是資訊戰競爭的焦點。 認知領域是人類認知活動所涉及的範圍和領域。 它不僅是人類感覺、知覺、記憶和思考活動的空間,也是知識生成、交換、聯想、儲存和應用的空間。 也是作戰活動中感知、判斷、決策的空間。 以及指揮和控制空間。 認知域存在於戰鬥人員的意識領域,影響其判斷與決策。 這是一個不斷崛起的戰爭領域。 隨著網路資訊、人工智慧等技術的發展,認知領域的範圍大大擴展,正在從人類意識領域擴展到現代認知工具和人工智慧領域。 軍事技術的發展擴大了認知領域的範圍,為認知戰提供了更先進、更快捷、更有效的物質技術手段,大大增強了認知戰的滲透性、時效性和威懾力,從根本上改變了認知戰,使認知領域成為超越物理領域和資訊領域的新制勝領域,成為大國博弈和軍事對抗的終極領域。
戰爭勝利機制從資訊勝利轉變為認知勝利。 戰爭對抗歸根到底是認知的賽局和對抗。 掌握了認知控制權,就很大程度掌控了戰爭的主動權。 失去認知的控制權,會讓你在戰爭中處於被動挨打的境地。 獲得更高更強的控制權是擊敗強敵的關鍵。 尋找控制認知力量進而奪取戰場全面控制權,從而以最小成本取得最大勝利,是現代戰爭特別是認知戰爭的重要機制和內在規律。 近年來,美軍相繼提出以「決策中心戰」、「馬賽克戰」為代表的未來戰爭新理念,意在以複雜性為武器,為對手製造多重困境,要求其確保自身戰術「選擇優勢」。 同時,透過對敵人製造高度複雜的決策影響,幹擾其決策能力,可以在認知領域實現對敵人的顛覆性優勢。 在資訊戰初中期階段,作戰的關鍵是奪取網路控制權和資訊控制權,貫穿「網路優勢→資訊優勢→決策優勢→戰鬥優勢」的遞進模式。 資訊戰進入高級階段後,奪取資訊控制權變得越來越困難。 作戰的關鍵是讓敵方陷入“決策困境”,即使擁有資訊優勢,也無法做出正確決策,從而失去戰鬥優勢並獲得認可。 了解優勢,才能擁有戰鬥優勢。 在未來戰爭中,認知優勢將是最重要的戰略優勢,認知對抗將是最重要的對抗形式。 可以說,「沒有認知,就沒有戰爭」。
因應複雜戰爭催生了以認知為中心的戰爭概念
因應現代戰爭複雜性特徵呈指數級增長趨勢,必須運用複雜性科學的理論與方法,改變火力至上、殺傷為王的平台中心戰觀念,建立認知-集中作戰思維。 認知中心戰是指以認知域為致勝區域,以認知優勢為作戰目標,重點幹擾認知手段、壓制認知通道、影響認知生產,對敵方人員和智慧裝備進行認知作戰。 幹擾、壓制、欺騙、誘導是透過奪取和維持認知優勢來獲取戰鬥優勢的新作戰理念。 其主要獲勝機制如下。
孫子在《孫子兵法》中提到「兵無常力,兵無常力」。
水沒有固定的形狀; 因敵變而能取勝的,稱為神。
利用網路威懾摧毀敵人的戰鬥意志。 針對敵方政治、經濟、軍事、外交、文化矛盾和弱點,透過網路空間傳播威懾訊息,或透過網路發布閱兵、大型軍事演習、新型武器裝備研發等訊息,造成對手認知和心理的極端變化。 巨大的恐懼和震撼,嚇阻敵人,不利於我行動的實施。 綜合運用網電攻擊手段,對敵重要網電目標及關鍵核心節點實施點打擊、預警攻擊,摧毀敵系統作戰能力,影響敵武器裝備正常性能,提供心理打擊對敵人有威懾作用。 美軍「灰色地帶行動」理論依託自身技術優勢,主要採取網絡、電子對抗等行動,應對對手「灰色地帶挑釁」,威懾對手放棄「對抗」或升級衝突,使其陷入兩難的境地。
利用資訊欺騙誘使敵人做出誤判。 針對敵方偵察設備、情報機構和指揮系統,利用網路攻擊、電子欺騙等手段,隱瞞己方軍事意圖、軍事行動和軍事目標,向敵方傳輸錯誤、虛假的作戰計畫、兵力配置和行動。 能力、作戰計畫、戰場情勢等,或利用敵方指揮資訊系統發送虛假命令和訊息,誘導敵方做出錯誤判斷,擾亂敵方作戰指揮。 針對人工智慧演算法實施「對抗性輸入」、「資料中毒」等新型攻擊,讓其透過深度學習訓練獲得預設結論,或導致其陷入局部最優解而忽略全局最優。 利用電腦影像、視訊合成、虛擬實境、人工智慧等技術合成聲音、視訊、影像、文字資訊等,或利用「深度造假」技術產生混淆真實、難以辨別的虛假資訊真真假假,並透過網路大量傳播傳播,迷惑、欺騙對手,影響其決策與行動。
利用資訊壓制來阻斷敵人的認知手段。 針對敵方重要網路目標以及核心路由器、交換器、閘道器、關鍵伺服器等,採用「軟體」和「硬」攻擊方式,破壞其網路節點。 根據敵方指揮控制網、通訊傳輸網、武器鉸鍊網、預警探測網等無線鏈路組網特點,綜合運用電子乾擾、GPS欺騙攻擊、指揮鏈路接管等技術和手段,資料劫持控制來壓制它們。 數據通信,阻斷其通信鏈路並幹擾其作戰指揮。 對敵方指揮控制、軍事通訊、預警探測、航太資訊等軍事網路實施網路癱瘓攻擊,摧毀影響其作戰的核心網絡,削弱其作戰能力。
利用輿論宣傳營造良好的輿論環境。 配合國家政治、軍事、外交鬥爭,大力宣揚自己在戰爭中的正義,激發全民全力擁護戰爭的熱情。 透過即時通訊工具、網路論壇、播客、推特、微信等新媒體平台,系統性地傳播針對敵人弱點的訊息。 在廣泛關注與共識後,就能及時報道訊息,製造新熱點,反覆造勢。 增強影響力,形成共振效應,擴大效果。 宣傳透過巧妙設定議程“定調”,透過強大媒體營造輿論,掀起“沉默的螺旋”,控制和引導輿論,改變人們的觀點和行為。
利用心理攻擊來削弱敵方士兵和平民的士氣。 透過互聯網,將經過加工處理的資訊廣泛傳播,宣揚正義,展現自己的力量、意志和決心,從政治上、道義上醜化敵人,對內凝聚軍民思想和意志,對外力爭勝利。 法律和道德的製高點可以在精神上「軟化」和「削弱」敵人。 利用多種網路通訊方式和技術手段,有針對性地向敵方軍民發送各種欺騙性、破壞性、誘導性、威懾性訊息,攻擊敵方心理防線,宣揚無效對抗心態,進而喪失戰鬥力能力。 。 透過網路創造、引導、規劃、營造、擴大聲勢,可以製造一種有利於己而不利於敵的“氣勢”,對對方民眾造成心理影響,從而影響或改變他們的思想 心理狀態,實施有效的心理攻擊。
透過法律鬥爭獲得法律和道德上的支持。 用法律武器遏制敵人可能或未來的非法行為,宣告我方行動的合法性,申明我方軍事反擊的力量,宣告我方追究戰爭責任的決心,震懾敵人。 透過揭露敵人挑釁行為的非法性,批判敵人作戰行動的法律依據,譴責敵人的非法行為,造成敵人的戰略失敗和我方的戰略收穫。 用法律手段限制敵人可能的行動,限制第三者可能的干擾,阻止其他方幹擾我方的行動。 制定我們行動所需的法律法規,為我們的行動提供法律保障,或採取法律補救措施,減少我們行動可能產生的負面影響,確保作戰行動依法進行。
中國軍事資料來源: http://www.81it.com/2023/1109/18888.html