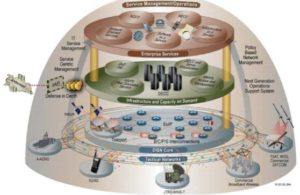
Chinese Military Informationization Trends – Cyber Integrated Battlefield // 中國軍事信息化趨勢 – 網絡綜合戰場
Source: PLA Daily
The army has given birth to the military and other military services. With the advent of the information age, the integration of battlefields and combat operations has made the integration of services a new trend and destination for the development of military construction.
Service integration: the general trend of informationized army construction
■Wang Xueping
The development of things often presents a spiral rising path, following the law of negation of negation. The development of human military activities, especially military construction, is also in line with this law. Before the information age, the army of the army was from one to many. The army had given birth to the sea and air. With the advent of the information age, the rapid development of technology has made the integration of military services a trend and a destination for the development of new military construction.
The future battlefield does not distinguish between land, sea and air
Under the condition of mechanization, the pattern of independent existence of land, sea, air and sky battlefields began to merge under the catalysis of the new military revolution. Multidimensional and multi-war occasions are the basic forms of the future battlefield.
The promotion of rapid development of science and technology. With the continuous development of science and technology and the improvement of mankind’s ability to control the battlefield, it is an inevitable trend that the battlefield will be dispersed from integration to integration. Science and technology are the driving force for the integration of battlefields and unlimited expansion into the air. The development of high-tech such as information technology, positioning and guidance technology has made the performance of weapons and equipment surpass the traditional land, sea and airspace boundaries. Global mobility, global arrival and global strike have become the targets of the development of the military of the world’s military power. The development of space situational awareness technology integrates surveillance, reconnaissance, intelligence, meteorology, command, control and communication, and integrates the battlefield information network to realize battlefield information sharing. Joint operations and precision strikes become the basic style of future warfare. The rapid development of space technology has made the surface information and the information of the global environment unobstructed. The expansion of the battlefield into space has condensed the traditional land, sea and air battlefields into one, becoming a stepping stone and pedal for the vast innocent space battlefield.
The inevitable evolution of the form of war. With the in-depth development of the new military revolution, the intensity of the war to informationization will further increase. Informatized warfare is not only a “speed war” but also a “precise war” and an “integrated war.” The acceleration of the war integration process is first manifested in the integration of land, sea and airspace, and the integration of the scope of the battlefield as the war develops. This is the basic condition for information warfare. The speed of war and the improvement of precision strike capability require that the military must have global maneuver, global combat and precision strike capability that transcends land, sea and air, cross-border, trans-ocean, and vacant, and battlefield integration is the basic guarantee. The war science and technology contest has intensified, and the requirements for battlefield resource sharing have become more obvious. Military personnel have broken through the geographical and military barriers and broke the boundary between land, sea and airspace. It is an important weight to win the war.
The requirements for quick fixes in combat objectives. Speed and precision are the main thrust of future wars. Eliminating battlefield barriers, integrating land, sea, air, and battlefields is the way to reach a speedy battle. The quickness and determination of the purpose of informatized warfare has promoted the integration of force preparation, equipment and operations. The integration of force preparation, equipment and operations has also promoted the arrival of battlefield integration. The military system is integrated into the arms and services. The scope of action has surpassed the narrow space of a single service. The ability to operate in a wide area and in a large space makes it difficult to divide the battlefield into a land battlefield, a sea battlefield, and an air battlefield. Weapons and equipment combines the performance of land, sea and air weapons. Its combat function surpasses the land, sea and airspace range, providing material conditions and support for battlefield integration. The strategic battle tactical action is integrated into one, the joint operations are divided into groups, the small squad completes the large task, and the informatized war characteristics of the tactical action strategy purpose will inevitably catalyze the dispersed battlefield toward one.
Signs of military integration appear quietly
While the development of science and technology is promoting the rapid birth of new arms, the cohesiveness of war integration is also affecting the integration of military construction. Under the conditions of informationization, the trend of integration of arms and services is becoming more and more obvious, and there is a tendency to accelerate development.
The theory of integration theory is repeated. The fusion of theory is a prelude to the integration of the military, and it is the magic weapon and sword to win the information war. Under the impact of the new military revolution, theoretical innovations have surpassed the waves, especially the integration of theoretical innovations aimed at joint operations. In order to adapt to the new changes in the form of war and the international pattern, in the 2010 “four-year defense assessment report” of the United States, the theory of joint operations of “sea and air warfare” was clearly put forward. In order to adapt to the requirements of the network-centric warfare, the French military integration theory innovation is at the forefront. The Army proposed the air-to-ground combat bubble theory, and the Navy proposed the theory of joint action from sea to land. The Indian Army has referenced and learned from the US “air-ground integration” and “quick-decisive” operational theories, and put forward the “cold-start” operational theory. The core is to strengthen the cooperation between the army and the sea and air force in order to seek the initiative of the operation and strive for the shortest time. The purpose of the battle is achieved within.
Integrated equipment surfaced. The rapid development of science and technology has continuously enhanced the comprehensive functions of weapons and equipment, and integrated equipment integrating land, sea, air and sky has become a material support and an important driving force for the development of military services. In order to win the initiative of integrated joint operations, the world’s military powers have accelerated the research and development of integrated equipment. The US military “Independence” stealth warship, which was once popular, is a very typical new integrated equipment. The ship integrates anti-submarine, mine-clearing, surveillance, reconnaissance and force deployment functions. It can carry three helicopters, some special forces and armored vehicles, and integrates the “ground and air” equipment. The ship-borne gun can carry out three-dimensional attacks on missiles launched from air, land and underwater targets, which greatly enhances the integrated combat capability of the equipment.
The integrated forces first appeared. The future informationized warfare is an integrated joint warfare operation carried out in multi-dimensional space such as land, sea, air, sky, and information. It is required that the participating troops must be an integrated military system. To meet this requirement, the army of the world’s powerful countries has intensified the construction of integrated forces. Joint expeditionary forces such as the US military include the Army Division, the Naval Aircraft Carrier Combat Group, the Marine Corps Division (sub-) and the Air Force Fighter Wing. The Russian military formed a mobile unit that spanned three services and one independent unit, including the Army’s Mobility Division, tank division, special brigade, rocket brigade, air force fighter, attack aircraft, bomber regiment, naval marine battalion and airborne troops. Airborne division. The rapid reaction force formed by France consists of different types of divisions of five arms. In accordance with operational needs, Germany has directly organized the Defence Forces into three units: the Intervention Force, the Stabilization Force and the Support Force. It can be seen that the integrated forces of multiple arms and services have become the direction of army construction and development in the information age.
Looking into the future, planning the army of today
The integration of the services and the ultimate integration are the inherent requirements of the information war and the basic law of the army’s construction and development. This law does not shift from people’s will. In order to seek the initiative of army building, we should follow this trend and make forward-looking decisions in promoting the integration of the military.
In-depth exploration of the theory of military integration. Theory is the forerunner of action, and it is the reflection on the top of the mountain. Aiming at the trend of the times, accumulating strength and finding countermeasures through theoretical research is the experience and practice of world-class military construction and development. The first is to strengthen the theoretical exploration of integrated construction. We should study the issue of integrated military construction as soon as possible, explore the construction goals, standards, paths, methods, and methods of the integrated military, and build bridges and paved roads for the military integration. The second is to strengthen the exploration of integrated operational theory. The development trend of military integration will inevitably bring about new changes in combat theory. It is necessary to strengthen the study of the characteristics of the integrated military operations, strengthen the study of integrated military operations and command methods, strengthen the study of the basic military tactics of the integrated military, and make forward-looking theories a traction in the development of military construction. The third is to strengthen the theoretical exploration of new talent training. To train new talents that meet the needs of the development of integrated military construction needs to be prepared in theory. The institutional structure, teaching content and teaching methods of colleges and universities need to focus on the law of integrated military construction and development, theoretically research, clear, and even through pilot exploration, so that the training of college personnel can adapt to the general trend of military integration development as soon as possible. For the development of integrated military construction, it is necessary to make a good talent reserve.
Accelerate the development of integrated equipment for the military. Integrated equipment is the material basis for the integration of services. In line with the general trend of the development of integrated military construction, our military should speed up the research and development of military integrated weapons and equipment. The first is the “collection” type of equipment. For example, the aircraft carrier-style “collection” type of equipment, with the hull as the basic platform, fuses fighters, artillery, anti-aircraft guns, missiles, and chariots into one, so that the equipment has the ability to multi-domain and multi-air combat. Our military should develop such “collection” type equipment based on land or sea or air, and promote the development of weapons and equipment to the integration of various arms and services. The second is the “all-round” type of equipment. In the future, the equipment must be able to run on the ground, fly in the air, swim in the water, and operate at high speed on the water, underwater, on land, and in the air, and the “human outfit” is integrated. The combatants follow the operational needs. Become a super equipment that “takes the sea and catches the moon, and picks up the moon.”
Explore the construction of a military united army. Comply with the general trend of the integration and development of the informatized military, actively promote the exploration of the construction of the military-integrated forces, and explore ways to accumulate experience for the development of military integration. Under the current circumstances, it is mainly necessary to build a large article on the integration of hybrid force preparation and create conditions for the integration of the military system. The establishment of a multi-service hybrid pilot unit will be rolled forward in actual combat training. Take the Army as an example, it is to build a hybrid force that integrates rifle, tan, gun, and land. For example, the integrated ground detachment consisting of armored forces, artillery, machine infantry, missile corps, attack and transport helicopter detachments, which was formed by the US Army, foreshadowed the development trend of integrated force formation that broke the arms and even the service line. With the accumulation of experience, the maturity of the conditions, and the improvement of the level of science and technology, the scope of the composition of the force has gradually expanded, and eventually an integrated experimental unit with complete strengths of the arms and services has been established.
Original Mandarin Chinese:
陸軍曾孕育了海、空等軍種。信息時代的到來,戰場、作戰行動的一體化,使得軍種融合成為新型軍隊建設發展的走向與歸宿——
軍種融合:信息化軍隊建設大趨勢
■王雪平
事物的發展往往呈現著螺旋式上昇道路,遵循著否定之否定的規律。人類軍事活動發展特別是軍隊建設也暗合著這種規律要求。在信息時代以前,軍隊的軍種是從一到多,陸軍曾孕育了海、空等軍種。而信息時代的到來,技術的迅猛發展使得軍種融合成為新型軍隊建設發展的走向與歸宿。
未來戰場不分陸海空天
機械化條件下,陸、海、空、天戰場獨立存在的格局,在新軍事革命的催化下開始走向融合,多維立體、多戰場合一是未來戰場的基本形態。
科技快速發展的推動。隨著科技的不斷發展和人類對戰場控制能力的提高,戰場由分散走向融合是必然趨勢。而科學技術則是戰場融合一體,並向空天無限擴展的推動力。信息技術、定位與製導技術等高新技術的發展,使武器裝備性能超越了傳統的陸、海、空域界線,全球機動、全球到達、全球打擊成為世界軍事強國軍隊發展的目標。空間態勢感知技術的發展,使監視、偵察、情報、氣象、指揮、控制和通信等融合一體,一體化戰場信息網絡,實現了戰場信息共享,聯合作戰、精確打擊成為未來戰爭的基本樣式。太空技術的快速發展,使地表信息和地球環境信息盡收眼底,戰場向太空的拓展,使傳統的陸海空戰場濃縮為一體,成為廣闊無垠太空戰場的墊腳石與踏板。
戰爭形態演變的必然。隨著新軍事革命的深入發展,戰爭向信息化演變的力度將進一步加大。信息化戰爭,既是“速度戰爭”,又是“精確戰爭”,更是“一體化戰爭”。戰爭一體化進程的加快,首先表現為陸域、海域、空域的融合,以及隨著戰爭發展而不斷拓展的戰場空間範圍的一體化,這是進行信息化戰爭的基本條件。戰爭速度與精準打擊能力的提升,要求軍隊必須具有超越陸海空界線,跨境、跨海、騰空的全球機動、全球作戰和精確打擊能力,而戰場一體化則是基本保障。戰爭科技較量加劇,戰場資源共享的要求更加明顯,軍事人才更衝破了地域、軍種壁壘,打破陸域、海域、空域戰場界線,是贏得戰爭的重要砝碼。
作戰目的速決的要求。速度與精確是未來戰爭的主旨。而消除戰場壁壘,融陸、海、空、天戰場為一體,則是達成戰爭速決的通道。信息化戰爭作戰目的速決性,推動了部隊編制、裝備、行動的融合。而部隊編制、裝備、行動的融合,又促進了戰場一體化的到來。部隊體制編制諸軍兵種融於一體,行動範圍已超越了單一軍種的狹小空間,廣地域、大空間行動的能力,使戰場很難再分為陸戰場、海戰場和空戰場。武器裝備集陸海空天兵器性能於一身,其作戰功能超越了陸域、海域、空域範圍,為戰場一體化提供了物質條件和支撐。戰略戰役戰術行動融於一體,聯合作戰分隊化,小分隊完成大任務,戰術行動戰略目的的信息化戰爭特性,必然催化分散的戰場走向一體。
軍種融合跡象悄然出現
科技發展在推動新軍兵種快速誕生的同時,戰爭一體化的內聚力也在牽動軍隊建設走向融合。信息化條件下,軍兵種一體化的趨勢日漸明顯,大有加速發展之勢。
一體化理論見解迭出。理論融合是軍種融合的前奏,更是打贏信息化戰爭的法寶與利劍。在新軍事革命大潮衝擊下,理論創新一浪高過一浪,特別是瞄準聯合作戰需要的一體化理論創新更是見解迭出。為適應戰爭形態和國際格局的新變化,2010年度美國《四年防務評估報告》中,明確提出了“海空一體戰”聯合作戰理論。為適應網絡中心戰的要求,法國軍隊一體化理論創新更是走在了前列,陸軍提出了空地作戰氣泡理論,海軍提出了由海向陸聯合行動理論。印度陸軍參考和借鑒美軍“空地一體”和“快速決定性”作戰理論,提出了“冷啟動”作戰理論,核心是強化陸軍與海、空軍的配合作戰,以謀求作戰的主動性,爭取在最短時間內達成作戰目的。
一體化裝備浮出水面。科技的快速發展,使武器裝備的綜合功能不斷增強,融陸、海、空、天於一身的一體化裝備不斷問世,成為軍兵種編制向一體化發展的物質支撐和重要推動力。為贏得一體化聯合作戰的主動權,世界軍事強國紛紛加快了一體化裝備的研發力度。曾經熱炒的美軍“獨立號”隱形戰艦,就是非常典型的新型一體化裝備。該艦融反潛、掃雷、監視、偵察和兵力部署綜合功能於一體,可載3架直升機、一些特種部隊和裝甲車,融“地空”裝備於一身。艦載炮可對空中、陸地和水下目標發射導彈進行立體攻擊,使裝備的一體化戰鬥力大大提升。
一體化部隊初見端倪。未來信息化戰爭,是在陸、海、空、天、信息等多維空間進行的一體化聯合作戰行動,要求參戰部隊必須是一體化的軍事系統。適應這一要求,世界強國軍隊紛紛加大了一體化部隊建設的力度。如美軍組建的聯合遠征部隊包括陸軍師、海軍航母戰鬥群、海軍陸戰隊部(分)隊和空軍戰鬥機聯隊。俄軍組建的機動部隊橫跨3個軍種和1個獨立兵種,包括陸軍的摩步師、坦克師、特種旅、火箭旅,空軍的戰鬥機、強擊機、轟炸機團,海軍的陸戰隊營和空降兵的空降師。法國組建的快速反應部隊由5個軍兵種的不同類型師組成。德國則根據作戰需求把國防軍直接編組為乾涉部隊、穩定部隊和支援部隊三種性質部隊。足見,多軍兵種一體化部隊已成為信息時代軍隊建設發展的方向。
放眼未來謀劃今日之軍
軍種融合,並最終走向一體,是信息化戰爭的內在要求,是軍隊建設發展的基本規律。這一規律不以人們的意志為轉移。謀求軍隊建設的主動性,我們就應該順應這一趨勢,在推進軍隊一體化建設上前瞻決策,未雨綢繆。
深入探索軍種一體理論。理論是行動的先導,更是“山頂”上的思考。瞄準時代走向,通過理論研究積蓄力量、尋找對策,是世界一流軍隊建設發展的經驗做法。一是加強一體化建設理論探索。應儘早研究一體化軍隊建設問題,探索一體化軍隊的建設目標、標準、路徑、方式、方法,為軍隊一體化建設從理論上搭好橋樑、鋪好路基。二是加強一體化作戰理論探索。軍隊一體化發展趨勢必然帶來作戰理論的全新變化。要加強一體化軍隊作戰運用的特點規律研究,加強一體化軍隊作戰行動和指揮方法研究,加強一體化軍隊基本戰法研究,讓前瞻性的理論成為軍隊建設發展的牽引。三是加強新型人才培養理論探索。培養適應一體化軍隊建設發展需要的新型人才,需要在理論上早做準備。院校的體制格局、教學內容、教學方法都需要著眼一體化軍隊建設發展規律,從理論上研究透,搞清楚,甚至通過試點探索,使院校人才培養儘早適應軍隊一體化發展的大趨勢,為一體化軍隊建設發展需要做好人才儲備。
加速軍種一體裝備研製。一體化裝備是軍種融合的物質基礎。順應一體化軍隊建設發展的大趨勢,我軍應加快軍種一體武器裝備的研發。一是“集合”型裝備。如航空母艦式的“集合”型裝備,其以艦體為基本平台,融戰機、火砲、高炮、導彈、戰車於一體,使裝備具有海陸空天多域多空作戰的能力。我軍應研發這種以陸或海或空為基本平台的“集合”型裝備,推進武器裝備建設向諸軍兵種融合一體方向發展。二是“全能”型裝備。今後的裝備要達到地上能跑、空中能飛、水中能遊,水上水下、陸上、空天都可高速機動作戰,而且“人裝”一體,戰鬥人員根據作戰需要隨進隨出,真正成為“下海捉鱉,上天摘月”的超能裝備。
進行軍種一體部隊建設探索。順應信息化軍隊一體化建設發展的大勢,積極推進軍種一體部隊建設探索,為軍隊一體化建設發展探索路子、積累經驗。當前情況下,主要應做好建設混合型部隊編制融合的大文章,為軍種體制編制走向一體創造條件。組建多兵種混合一體試點部隊,在實戰訓練中滾動推進。以陸軍為例,就是建設融步、坦、炮、陸航等兵種於一體的混合型部隊。如,美陸軍組建的由裝甲兵、砲兵、機步兵、導彈兵、攻擊與運輸直升機分隊組成的一體化地面分隊,預示了打破兵種甚至軍種界線的一體化部隊編制的發展趨勢。隨著經驗的積累、條件的成熟,以及科技水平的提高,部隊力量構成的範圍逐漸擴大,最終組建成軍兵種力量齊全的一體化試驗部隊。
Original referring url: http://www.mod.gov.cn/mobilization/2017-07/28/