Analysis on the Establishment of the Joint Operation Command System by the PLA
中國軍方聯合作戰指揮中心解放軍建構聯合作戰指揮體制評析國防
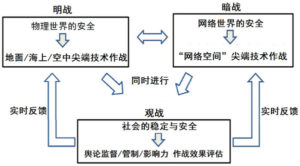
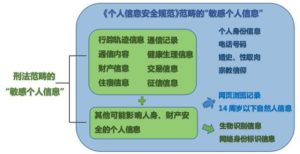
1 六、解放軍建構聯合作戰指揮體制評析 國防大學政治系馬振坤教授 ■ 習近平在去(2015)年 11 月下旬召開中央軍委改革工作會議, 強調要組建戰區聯合作戰指揮機構和健全軍委聯合作戰指揮 機制,以強化軍隊聯合作戰能力。
■ 改革重點在建立一套能夠上下銜接、起承轉合之聯合作戰指 揮中樞機制,在中央軍委層級是將現有總參謀部改組成為直 屬中央軍委之聯合參謀部,對上能讓軍委主席有效行使最高 軍令指揮權;對下則能夠銜接整合各戰區聯合作戰指揮系統。
■ 解放軍在理順組織結構及權力運作模式後,將在組織編制、 軍種功能、武器裝備以及作戰指揮各個面向趨向成熟,可望 提升其作戰能力。

(一)前言 中共於去(2015)年 11 月下旬召開中央軍委改革工作會議,正式 揭開軍隊組織變革之序幕。中央軍委深化國防和軍隊改革領導小組組 長習近平在會中發表重要講話,直指解放軍「必須在 2020 年前在領 導管理體制、聯合作戰指揮體制改革上取得突破性進展、在優化規模 結構、完善政策制度、推動軍民融合發展等方面改革上取得重要成 果,努力構建能夠打贏信息化戰爭、有效履行使命任務的中國特色現 代軍事力量體系,完善中國特色社會主義軍事制度」。
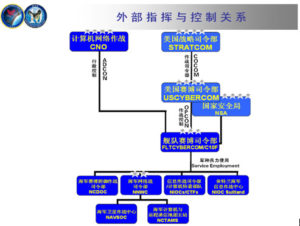
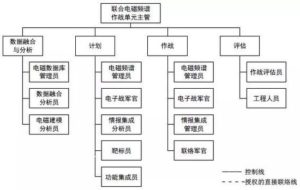
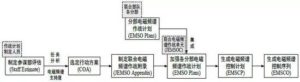
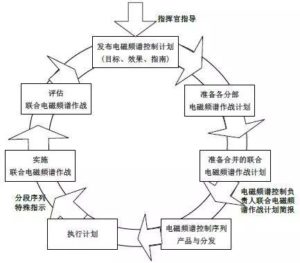
(二)解放軍作戰指揮體系的變革 在習近平揭櫫的軍隊改革具體內容上,他強調要組建戰區聯合作 戰指揮機構和健全軍委聯合作戰指揮機制。透過中央軍委組織職能調 整之頂層設計,習近平要建構「軍委→戰區→部隊」的作戰指揮體系 以強化軍隊聯合作戰能力。 解放軍原本並無聯合作戰指揮體制,其既有之作戰指揮體制係以 從事境內地面持久作戰為主之設計,具體表徵有二,一是解放軍並無 2 陸軍司令部,但海空軍及二炮部隊則自其組建時即成立軍種司令部; 二是中共將全中國大陸劃為七大軍區,作戰時以軍區為基礎轉換為戰 區,採取誘敵深入之戰略遂行地面持久消耗戰。 解放軍僅有海空二炮司令部卻無陸軍司令部並非獨特設計,而是 歷史發展的結果。中共自 1927 年創立紅軍成為其首支武裝力量,至 1949 年組建海軍和空軍之前,其軍隊皆以地面部隊為主,在國共內 戰期間,為方便作戰指揮,堅持以黨領軍以及強化後勤保障,中共在 軍事領導上,採取總部形式作為其軍隊領導管理和作戰指揮機構。而 中共在建政後仍然延續此總參謀部、總政治部、總後勤部之架構,作 為其軍隊領導體制,即便陸續組建海空軍及二炮部隊,並未改變此架 構,反而是將新組建的軍兵種納入此架構中,成為支援地面部隊作戰 的輔助性軍兵種。 因此中共傳統的四大總部領導機制,係以陸軍為主、海空軍及二 炮部隊為輔、適合從事傳統單一軍種地面作戰的軍隊領導機制。此機 制無法適應現代戰爭係屬遠程投射、立體攻防、不同軍兵種聯合作戰 之特性,共軍內部早有變更之議。尤其近年來中共與周邊國家在陸地 領土主權爭議逐漸經由雙邊協商談判獲得解決、陸地邊界之緊張情勢 明顯降低之際,在東海及南海之島礁領土主權及海域劃界爭端卻日形 嚴重。而對應此等緊張情勢者,是海空二炮等軍兵種而非陸軍,爭端 發生之東海、南海區域,亦非南京、廣州軍區戰備任務指向之處。 若依中央軍委賦予兩大軍區之任務,南京軍區是「主管江蘇、安 徽、浙江、江西、福建、上海五省一市軍事事務的大軍區,主要作戰 使命是保衛南京、上海、杭州、福州等東南沿海發達的特大城市和工 業區的安全」。依此內容視之,南京軍區主要作戰範圍並不包括東海 及釣魚臺。再依共軍廣州軍區之主要任務內容視之,該軍區是解放軍 「主管廣東、廣西、湖北、湖南、海南五省區軍事事務的大軍區,戰 時使命為保衛中國南部,尤其防止越南和東海沿海的攻擊,防衛廣 州、深圳等特大城市。此外,當需要時也負責增援香港和澳門」。同 樣地,廣州軍區防務亦不包括南海諸島礁。 3 除大軍區主要戰略方向係向陸而非向海,大軍區指揮職位的設計 上也是以陸軍為主,七大軍區司令員均由陸軍將領出任,各軍區海空 軍司令員在編制上僅為大軍區之副司令員,故軍區海空軍主要作戰任 務係以支援軍區地面部隊作戰為主,而非遂行境外海空域獨立作戰。 但依據中共公布之「2015 中國的軍事戰略報告書」,共軍要「加 快轉變戰鬥力生成模式,運用信息系統把各種作戰力量、作戰單元、 作戰要素融合集成為整體作戰能力,逐步構建作戰要素無縫鏈接、作 戰平台自主協同的一體化聯合作戰體系」,另要「按照權威、精幹、 靈便、高效的要求,建立健全軍委聯合作戰指揮機構和戰區聯合作戰 指揮體制」。顯見中共領導階層深知既有中央軍委與各總部、軍種司 令部間職能區分,以及大軍區制度等,皆無法因應未來戰爭聯合作戰 型態之需求,因而藉由中央軍委組織調整的時機,對於軍隊領導管理 體制和聯合作戰指揮體制進行一體化設計。 (三)現行聯合作戰指揮機構的組建 依據「意見」,為適應一體化聯合作戰指揮要求,應「建立健全 軍委、戰區兩級聯合作戰指揮體制,構建平戰一體、常態運行、專司 主營、精幹高效的戰略戰役指揮體系」,且要「重新調整劃設戰區」。 在軍隊作戰指揮體系上,則要「按照聯合作戰、聯合指揮的要求,調 整規範軍委聯指、各軍種、戰區聯指和戰區軍種的作戰指揮職能」, 部隊訓練則要求必須「與聯合作戰指揮體制相適應,完善聯合訓練體 制」。 在具體組建聯合作戰指揮機構方面,在中央軍委層級是將現有總 參謀部改組成為直屬中央軍委之聯合參謀部,此新成立之「聯參」只 負責中央軍委之聯合作戰指揮事宜,與過去的「總參」總攬對軍隊的 作戰指揮權和領導管理權有很大的差異。更重要者,新的聯合參謀長 不再擁有過去總參謀長對軍隊之最高軍令權,此最高軍令權在中央軍 委職能調整之後,已回歸到中央軍委主席之手,以落實軍委主席負責 制之精神。此聯合參謀部只是一個直屬中央軍委常態存在之作戰指揮 4 機構,故聯合參謀長不論在平時或戰時,都扮演軍委主席在行使軍隊 作戰指揮最高軍令權之幕僚長,而不再是過去總參謀長名為幕僚長, 實際上卻擁有等同陸軍司令員之權力。 將總參謀部改編成為聯合參謀部在具體實踐上確實可行,因為目 前總參謀部除陸軍出身之總參謀長、副總參謀長外,海、空、二炮皆 有擔任副總參謀長,其實已具備聯合作戰指揮機制之雛型。此海空二 炮擔任副總參謀長之將領在原本制度運作下,即是未來接任海空二炮 司令員之必然人選,其在副總參謀長任內,可獲得與其它軍種副總參 謀長溝通協調之經驗,並可在此過程中了解其它軍種之特性以及在執 行作戰任務時必須考量之諸種條件。當此將領擔任軍種司令員後,在 落實中央軍委「一體化聯合作戰」政策要求下,自當能夠與其它軍種 溝通協調,降低軍種本位主義色彩。 海空二炮將領出任總參副總參謀長始於江澤民在 2004 年將中央 軍委主席職務交棒給胡錦濤時,同步將海空二炮司令員納入中央軍委 成員起。原本海空二炮司令員之級別等同大軍區正職,僅同陸軍之大 軍區司令員。江澤民將其納入中央軍委後,海空二炮司令員級別提 升,但是在司令員以下各階則無變動,尤其各大軍區空軍司令員以及 瀕海大軍區海軍司令員,在級別上仍屬大軍區副職,編制上為軍區副 司令員。為求幹部梯隊之完整性和連續性,並且符合不同軍兵種聯合 作戰之時代發展趨勢,乃在總參謀部原本由陸軍壟斷之副總參謀長職 務,分由陸、海、空軍和二炮之將領分別擔任,以連接海空二炮軍兵 種高階將領在成為軍兵種司令員之前最後階段職務歷練。 除副總參謀長層級外,總參謀部所屬各部例如情報部、作戰部 等,亦早已納入海空二炮各軍兵種幹部擔任高階參謀,各自負擔與本 身軍兵種相關之情報、作戰等參謀業務。換言之,總參謀部在過去十 年來即是以滿足不同軍兵種聯合作戰之需求作為主要發展方向,且實 際上已發展出成熟的聯合作戰指揮參謀機制。因此將總參謀部調整為 聯合參謀部,就實質運作面而言,並非是全盤的改變,反而是將實質 上已初步具備的聯合作戰機制加以制度化與正名化。 5 因此將總參謀部調整為聯合參謀部之重點並不在總參謀長、副總 參謀長等領導層級職務由不同軍種將領擔任,亦不是整合不同軍種作 戰參謀業務,而是建立一套能夠上下銜接、起承轉合之聯合作戰指揮 中樞機制。對上能夠落實中央軍委主席負責制之精神,讓中央軍委主 席得以透過聯合參謀部之機制,有效行使最高軍令指揮權;對下則能 夠銜接整合各戰區聯合作戰指揮系統,讓一體化聯合作戰指揮體制成 為一個「有機的整體」,在作戰指揮上不會出現「斷鏈」甚至「無鏈 結」的情況。 建立聯合作戰指揮機制在大軍區層級,即是取消現有的七大軍 區,另成立東西南北四大戰略方向之戰區,以及保障北京安全之中部 戰區。傳統上,大軍區是中共軍隊體制上的主要建制,自毛澤東時期 強調誘敵深入境內決戰的戰略思維下,大軍區制度即扮演最重要之分 區屯兵固守防衛角色。事實上,大軍區是真正掌握軍隊、集軍隊之軍 令軍政權於一身的體制,舉凡軍隊之建設、教育訓練、乃至作戰指揮 權,皆由大軍區司令員掌握。另外中共政權在國防動員體制和軍地制 度,也都依托在大軍區體制之下,與維護內部安全秩序相關之武警部 隊之建制與指揮,也都在大軍區管轄範圍內。 由於大軍區制度是以屯兵和境內決戰為前提,在體制運作上自然 以陸軍為主,海空軍及二炮僅扮演支援陸軍作戰的角色。隨著中共軍 事現代化成果日顯,海空二炮遠距投射力量不斷強化,共軍向海方向 的活動範圍不斷擴張,軍事戰略思維已改採邊境和境外作戰,不再以 誘敵深入境內決戰為主。而境外作戰自然以能夠從事遠距投射之海空 軍和二炮作戰力量為主,陸軍反而僅能扮演預備隊之角色。因此將以 陸軍為主之大軍區體制改為以不同軍兵種遂行聯合作戰為主之戰區 指揮體制,方能整合不同軍兵種之作戰力量,即時且有效發揮海空二 炮遠距投射火力之優勢。 另外,將大軍區改為戰區,亦可消除原本大軍區司令員壟斷軍隊 領導及指揮權,形同分地割據之軍閥的現象。戰區將僅負責聯合作戰 指揮,戰區司令員僅擁有對其戰區之聯合作戰指揮權,並不擁有對軍 隊之領導管理權。軍隊領導管理權由各軍種司令部掌握,如此可以將 6 軍令權和軍政權在戰區層級完全切割,就不會再出現軍區司令員形同 地方軍閥的權力膨脹問題。
(四)結語 習近平在此次中共中央軍委組織調整中,展現對軍隊完全的領導 權威。誠然外界多認為習近平通過這次軍改刻意打亂軍中既有的權力 結構,清洗原本在軍隊裡根深蒂固的江澤民派系將領,全面掌握軍 權。但是平心而論,從中央軍委公布的「意見」對中央軍委層級、軍 種司令部層級、以及戰區層級的組織調整內容看來,這次的變動若能 落實,的確可以讓解放軍的組織架構及權力運作機制脫胎換骨。解放 軍在理順組織結構及權力運作模式後,將在組織編制、軍種功能、武 器裝備以及作戰指揮各個面向趨向成熟,符合現代化軍隊的標準,而 這也將讓解放軍的作戰能力在可預見的未來呈現出跳躍式之進步。

English Translation
Analysis on the Establishment of the Joint Operation Command System by the PLA
China National Defense University

■ Xi Jinping held a meeting to reform the Central Military Commission in late November (2015).
Emphasizing the need to establish a joint combat command organization in the theater and a joint combat command of a sound military commission
Mechanism to strengthen the joint combat capabilities of the military.
■ The focus of the reform is to establish a set of joint operations that can be linked up and down.
The central mechanism, at the Central Military Commission level, is to reorganize the existing general staff into straight the Joint Chief of Staff of the Central Military Commission is able to effectively exercise the highest authority for the chairman of the Central Military Commission Military command structure; to the next can be integrated with all theater joint warfare command systems.
■ After the People’s Liberation Army clarifies its organizational structure and power operation mode, it will organize
The military services, weapons and equipment, as well as operational commanders, tend to be mature.
Improve its combat capabilities.
(I). Introduction
The Chinese Communist Party held a meeting to reform the Central Military Commission in late November (2015).
Reveal the prelude to the reform of the military organization. The Central Military Commission Deepens the Leading Group for National Defense and Army Reform
President Xi Jinping delivered an important speech at the conference, pointing to the People’s Liberation Army “must be in the lead by 2020
Led to breakthroughs in the reform of the management system and joint operations command system, and the optimization of scale major achievements have been made in reforming the structure, improving policies and systems, and promoting the integration of military and civilian development.
As a result, efforts will be made to build Chinese characteristics that can win informatized warfare and effectively fulfill its mission.
On behalf of the military strength system, improve the socialist military system with Chinese characteristics.”
(II) The reform of the PLA command system
In Xi Jinping’s disclosure of the specific contents of the military reform, he emphasized the need to establish a joint cooperation.
The joint command and command mechanism of the war command organization and the sound military commission. Through the Central Military Commission organizational functions
With the entire top-level design, Xi Jinping must build a combat command system of “military committee, theater, and troops”.
In order to strengthen the joint combat capabilities of the military.
The People’s Liberation Army originally did not have a joint operational command system. Its existing operational command system was engaged in the design of long-term operations on the ground in the Mainland, and there are two specific characterizations. One is that the PLA did not the Army Command, but the Hainan Air Force and the Second Artillery Corps established the Service Command since its establishment;
Second, the Chinese Communist Party has designated the entire Chinese mainland as the seven major military regions and converted to combat based on the military region.
District, adopting a strategy to lure the enemy into a long-lasting war of attrition.
The People’s Liberation Army’s only air and sea artillery headquarters but no army headquarters are not uniquely designed, but the result of historical development. The Chinese Communists founded the Red Army as its first armed force since 1927.
Prior to the formation of the Navy and the Air Force in 1949, its troops were mainly based on ground forces within the KMT.
During the war, in order to facilitate combat operations, adhere to the leadership of the party and strengthen logistics support, the Chinese Communist Party
In terms of military leadership, it takes the form of headquarters as its military leadership management and operational command organization. And after the establishment of the government, the Chinese Communist Party continued the structure of the General Staff Headquarters, the General Political Department, and the General Logistics Department.
For its military leadership system, even if the navy, air force, and second artillery units were successively formed, they did not change this plane.
Instead, the newly-formed military units are included in this structure and become support for ground forces operations.
Combines & Auxiliary arms.
Therefore, the four traditional leadership mechanisms of the Chinese Communist Party are based on the Army, the Hainan Air Force and the Second Supplementary to the artillery force, it is suitable for the army leadership mechanism for traditional single-army ground operations. This machine system cannot adapt to modern warfare, long-range projection, three-dimensional offensive and defensive, joint operations of different types of arms
The characteristics of the Communist Army have long been changed. In particular, the CCP and its neighboring countries have been on land in recent years.
Territorial sovereignty disputes are gradually resolved through bilateral negotiation and tension on the land boundary.
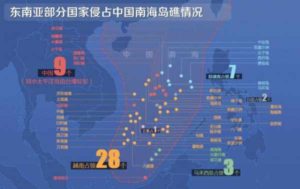
At a time of marked decline, disputes over the territorial sovereignty and maritime delimitation of the islands and reefs in the East China Sea and the South China Sea were observed.
serious. The counterparts to these tense situations are the Hainan Second Artillery Corps and not the Army.
The East China Sea and South China Sea areas that occurred were also not directed by the combat readiness tasks of the Nanjing and Guangzhou military regions.
If the tasks assigned to the two military regions are assigned by the Central Military Commission, the Nanjing Military Region is “supervising Jiangsu and An.
Military areas of the five provinces and one city of Anhui, Zhejiang, Jiangxi, Fujian and Shanghai
The mission is to defend the developed mega cities and workers in the southeast coasts of Nanjing, Shanghai, Hangzhou and Fuzhou.
Industry Zone Security”. According to this content, the main battle area of the Nanjing Military Region does not include the East China Sea.
Diaoyutai. According to the main tasks of the Communist Army of the Guangzhou Military Region, the military region is the People’s Liberation Army.
“In charge of military affairs in the five provinces and regions of Guangdong, Guangxi, Hubei, Hunan and Hainan
Mission to defend southern China, in particular to prevent attacks on the coasts of Vietnam and the East China Sea.
State, Shenzhen and other megacities. In addition, it is also responsible for the reinforcement of Hong Kong and Macao when necessary.” with
In the sample plot, the defense of the Guangzhou Military Region does not include the South China Sea Islands.
In addition to the major strategic directions of the military region, the design of command posts in the large military region is directed toward the land instead of to the sea.
The Army is also the main force, and the commanders of the seven military regions are all served by army generals.
The military commander is only the deputy commander of the military area in the preparation, so the main combat operations of the Hainan Air Force in the military region
The Department is mainly to support the ground forces of the military region, instead of independently operating in the offshore airspace.
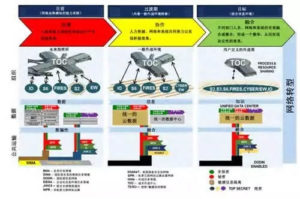
However, according to the “2015 China Military Strategy Report” announced by the Chinese Communist Party, the Communists must “add
Rapidly change the combat power generation mode and use information systems to put various combat forces and units of combat
Combine operational elements into integrated combat capabilities, and gradually build combat elements to make seamless links.
The integrated joint combat system where the platform is autonomously coordinated with each other” must also be “according to authority, capable, and effortlessly and efficiently required to establish and improve joint operations of the Central Military Commission and joint operations in the theater
Command system.” It is evident that the leadership of the Chinese Communist Party is fully aware of the existence of both the Central Military Commission and headquarters and the Military Services Division.
The division of functions among different ministries, and the military area system, etc., cannot meet the requirements of future warfare joint operations.
The demand of the type, and therefore the time for the adjustment of the Central Military Commission, for the leadership of the military
The system and the joint operational command system are designed in an integrated manner.
(3) Establishment of the current joint operations command organization
According to “opinions,” it is necessary to “establish and improve the
The two-level joint combat command system of the Central Military Commission and the theater establishes an integrated peacetime operation, normal operation, and
Main, lean and effective strategic battle command system, and “re-adjust the planning of the theater.”
In the military operational command system, it is necessary to “adjust the requirements of joint operations and joint efforts to standardize the operational command functions of the Central Military Commission, the Military Services, the Joint League Forces, and the regional military services.”
The training of troops requires that “it must be adapted to the joint combat command system and improve the joint training body system”.
In the specific formation of a joint combat command organization, at the Central Military Commission level will be the existing total the Staff Department was reorganized into a joint staff department directly under the Central Military Commission. This newly established “joint participation” is only
Responsible for the Joint Combat Command of the Central Military Commission, and the “Gan Sen General” of the past there is a big difference between operational command and leadership. More importantly, the new Joint Chief of Staff
No longer has the highest military commander of the general staff in the past. The highest military authority is in the Central Army.
After the adjustment of the committee’s functions, it has returned to the chairman of the Central Military Commission to implement the responsibility of the chairman of the Central Military Commission.
The spirit of the system. This Joint Staff is just a direct command of the Central Military Commission.
Institutions, so the chief of the Joint Chiefs of Staff, both in peacetime and in wartime, plays the role of the chairman of the Central Military Commission in the exercise of the military.
The commander of the highest military command of the combat commander is no longer the chief of general staff of the past.
In fact, it has the same power as the army commander.
The restructuring of the General Staff Headquarters into the Joint Staff Department is indeed feasible in the specific practice because in addition to the chief of the general staff and deputy chief of the general staff of the former general staff of the former general staff, the sea, air, and the second gun are all
As the deputy chief of the general staff, in fact, he already has the prototype of joint operations command mechanism. This sea and air two the commander of the deputy chief of the general staff of the cannon, under the operation of the original system, is to take over the sea and air artillery.
The commander is an inevitably elected candidate who can be obtained as a deputy chief of the general staff and can be used as a deputy general secretary of other services.
Communicate the experience of communication and coordination, and understand the characteristics and the conditions that must be considered when performing combat missions. After this general served as commander of the military,
Implementing the Central Military Commission’s “integrated joint operations” policy requires that it be able to cooperate with other service communicate and coordinate, reducing the service-oriented nature.
The Hainan Second Artillery general served as deputy chief of general staff of the General Staff and began with Jiang Zemin in 2004.
When the chairman of the Central Military Commission delivered the post to Hu Jintao, he simultaneously incorporated the commander of the Hainan Second Artillery into the Central Military Commission.
Members from. The level of the original commander of the Haikong Second Artillery was equal to that of the Great Military Region, which was only equal to that of the Army.
Commander of the Military District. After Jiang Zemin incorporated it in the Central Military Commission, the commander of the Second Air and Sea Artillery ranks but there are no changes in the order of the commander, especially the commanders of the air forces of the major military regions.
The naval commander of the Bohai Sea Military Area Command is still a deputy chief of the military region at the rank, and the military commander is assigned to the military region.
Commander. In order to achieve the integrity and continuity of the cadre echelon, and to meet the requirements of different military units
The trend of development in the era of warfare is that of the deputy chief of the general staff who was originally monopolized by the Army in the General Staff Department.
The service is divided into the positions of generals of land, sea, air force, and second artillery to connect the Hainan Second Artillery Corps.
The high-ranking generals took the final stage of career training before becoming military commanders.
In addition to the rank of deputy chief of the general staff, all departments under the general staff department such as the intelligence department and the warfare department
And so on, they have long been included in the cadres of the sea, air, and the Second Artillery, serving as high-level staff, and their respective burdens.
Armed Forces related intelligence, operations and other staff officers. In other words, the General Staff in the past ten years and in recent years, it is to meet the needs of joint operations of different types of arms as the main direction of development.
At the same time, a mature joint combat command staff mechanism has been developed. So it must adjust the General Staff to The Joint Staff, in terms of substantive operations, is not a complete change, but instead it will
The joint warfare mechanism that has been initially established has been institutionalized and renamed.
Therefore, the focus of adjusting the General Staff Department to the Joint Staff Department is not the chief of the general staff and vice president.
Chiefs of Staff such as the Chief of Staff are served by generals of different services and are not integrated into different military services.
Instead of consulting staff, establish a set of joint operations command that can be linked up and down, inherited from each other the central mechanism. In order to implement the spirit of the responsibility system of the chairman of the Central Military Commission, the Central Military Commission should be
Can effectively exercise the highest military command authority through the mechanism of the Joint Staff Headquarters; enough to integrate and integrate the joint operations command systems of all theaters and make the integrated joint operations commander
As an “organic whole,” there will be no “broken chain” or even “no chain” in combat command Results”.
The establishment of a joint combat command mechanism at the rank of the military region is to cancel the existing seven major military units.
District, the establishment of a four-strategic direction of the East, West, South and North, and the security of Beijing Theater. Traditionally, the large military area is the main organizational system of the Chinese Communist Army, since Mao Zedong’s time under the strategic thinking of emphasizing the lure of the enemy’s deep defensive battles in the country, the major military region system plays the most important role.
District soldiers stick to the defensive role. In fact, the military area is the army that truly controls the army and sets up the army.
The system of the military regime, which includes the construction of the army, education and training, and even combat command
The power is controlled by the commander of the military area. In addition, the Chinese Communist regime’s national defense mobilization system and military and land system
Degree, also relying on the system of the great military region, and related to the maintenance of the internal security order of the armed police department
The formation and command of the team are also within the jurisdiction of the military area.
Since the military region’s system is based on the premise of setting up troops and a decisive battle in the country, it is natural to operate the system.
Mainly based on the Army, the Hainan Air Force and the Second Artillery only played the role of supporting the Army. With the Chinese Communists the achievements of modernization have become increasingly apparent.
The scope of activities has continued to expand, and military strategic thinking has shifted to border and foreign operations.
Luring the enemy into the depths of the domestic decisive battle. However, it is natural for overseas operations to be able to engage in distant projections.
The Army and the Second Artillery are the main combat forces, but the Army can only play the role of reserve force. So will the army-based major military zone system was changed to a combat zone based on joint operations between different types of military units.
The command system can only integrate the combat forces of different military units, and immediately and efficiently this weapons combination has the advantage of projecting firepower from a distance.
In addition, changing the military area into a theater can also eliminate the original military commander’s monopoly of the military.
Leadership and command rights are similar to the phenomenon of the warlords split by land. The theater will only be responsible for joint operations commanding, the commander of the theater has only joint warfighting command over the theater and does not possess military command.
The leadership of the team. The leadership of the army is controlled by the various service commands so that the military commander and the military regime are completely cut at the theater level, and military commanders will no longer appear.
The issue of the expansion of power of local warlords.


(4) Conclusion
Xi Jinping demonstrated complete leadership over the army during the restructuring of the Central Military Commission of the CPC authority. It is true that the outside world thinks that Xi Jinping deliberately disrupted the existing power in the military through this military reform.
Structure, cleansing Jiang Zemin faction generals deeply rooted in the army and fully grasping the military right. But in all fairness, the “opinions” announced by the Central Military Commission of the Central Military Commission ranks and forces.
The level of organizational adjustment at the command level and the theater level suggests that if this change can implementation can indeed make the PLA’s organizational structure and power operation mechanism reborn.
People’s Liberation Army
After the military has straightened out the organizational structure and power operation mode, it will organize the organization, military services, and military operations.
Equipment and combat operations are oriented toward maturity and meet the standards of modern military forces.
This will also allow the PLA’s combat capabilities to show a leap forward in the foreseeable future.




.
Chairman Xi inspects the CMC’s joint operations command center and has aroused strong reaction in the entire army and the armed police force
Comprehensively improve the ability to prepare for fighting in the new era and provide strategic support for the realization of the Chinese dream
“To realize the party’s goal of strengthening the army in the new era and building the people’s army into a world-class army, we must grasp the key to fighting wars and defeating warlords. We have a major step forward in preparation for war.” On the 3rd, Chairman Xi Jinping inspected the Central Military Commission. The Operation Command Center led a group of CMC members to study the construction of the CMC Central Committee, and talked with the officers and men of the relevant task forces stationed at the Frontier Defense and Coastal Defence, inspected the Djibouti Security Base through the video, listened to the report of the PLA’s military preparation for war preparations, and delivered an important speech. It caused strong repercussions in the entire army and the armed police forces.
The officers and men all said that this inspection fully embodies President Xi’s high attention to the issue of military preparations for fighting warfare. This shows that the new military committee has implemented the spirit of the party’s Nineteenth Congress and promoted the work of the entire military to fight and win. A clear-cut attitude. They said that we must conscientiously study and implement the spirit of the Nineteenth National Congress of the Communist Party of China, adhere to the guidance of the military ideology of Xi Jinping, implement the military strategy under the new situation, strengthen the mission, strengthen reforms and innovations, intensify work implementation, and comprehensively improve preparations for fighting in the new era. The ability to provide strategic support for the realization of the “two hundred years” goal and the Chinese dream of realizing the great rejuvenation of the Chinese nation.
Tighten the string of war preparations and strengthen war preparations.
On the morning of the 3rd, the coldness hit people outside the window, but the joint military command center of the Central Military Commission was warm and strong. President Xi once went to the Central Building of the Central Committee of the Central Committee of the Central Military Commission, and led a group of people in the Central Military Commission to study the construction of the Central Committee of the Central Military Commission.
“When Xi Chairman made an inspection, he delivered an important speech and profoundly clarified the strategic significance and practical requirements for comprehensively improving the ability to prepare for fighting in the new era.” Zhou Shangping, deputy director of the Joint Operations Department of the Central Military Commission of the Central Military Commission who inspected the entire process, said, “This is the leader of the party. The commander of our army piloted the People’s Army to implement the party’s strong military objectives in the new era, to build a world-class army, and to send political mobilization and epoch orders to the entire army.”
The military is preparing to fight. The fundamental focus of the people’s army in carrying out missions in the new era is combat effectiveness.
The officers and men of the various theaters, services, and agencies of the Central Military Commission said in their discussions that the officers and men of the entire army must only tighten the war preparedness string, strengthen war preparations for war preparations, and always focus on preparing for battles and continuously improve their ability to win. Situation, control crisis, curb war and win war.
“If you want peace, then you have to prepare for war.” The party’s 19th representative Wang Jinlong served as an instructor. A certain army brigade in the central theater “does a great deal”. In the war years, he played in the name of He Huwei. In the new era, the company has a long history. The brigade is responsible for the mission of the brigade for emergency combat readiness. It always maintains a state of readiness for action on the string. He believes that the state is uneasy and that it will be dangerous to forget. Things in the world are always the same. If you are not ready, the enemy will come. You are ready. The enemy does not dare to come. The dialectic of war and peace tells us that if we can fight, we will not be able to fight unless we are ready to fight.
“We must engrave the word ‘war’ in our hearts and continue to strengthen our sense of responsibility for ‘ready to go on the battlefield’. We will deeply engrave our duty to prepare for war and become a conscious action,” said Cui Jiabin, a brigade commander of the Army Aviation Corps. Once something can be quickly responded, resolutely fulfill the tasks entrusted by the Party Central Committee, the Central Military Commission and President Xi, and resolutely safeguard national sovereignty, security, and development interests.
Pay close attention to actual combat military training and improve the ability to win
Socialism with Chinese characteristics has entered a new era, and national defense and army building have also entered a new era.
The officers and men believe that the new era requires that the military must have new capabilities, but to have new capabilities, it is necessary to take substantive training.
“When Xi inspected the Central Committee of the Central Military Commission, Xi pointed out that we must focus on deepening military training in actual combat, stick to how to train soldiers on how to train, and what to do if we need to fight, and inspire the enthusiasm, initiative, and creativity of the officers and men. The military has risen vigorously in the military training upsurge,” said Liu Rui, the 19th Party Congress representative and head of the Air Force’s aviation regiment. “I’m most impressed by this. The military is only holding on to actual combat military training and improving their ability to win. Only in this way can we shoulder the mission of the mission of the new era given by the party and the people.”
Liu Rui is the first air force of the Air Force to modify the H-6K air force and is an important force in the air force’s long-range offensive operations. At this time after the closing of the 19th National Party Congress, he not only preached the spirit of the Nineteenth Party Congress, but also spent all his time on the training ground. A few days ago, he organized and implemented the largest cross-regional mobile combat training in the team’s history. From dawn to late at night, from combat to ultra-low altitude, from land to sea, all the way to the road, across multiple strange areas. And several airports, lasting more than 9 hours, with a range of nearly 5,000 kilometers…
A synthetic brigade of “Huangcailing Mountain” of the 74th Army Group of the Southern Theater Army is currently training hard soldiers to welcome the coming year-end assessment of the group army. Instructor Chen Yuwen believes that President Xi inspects the Central Military Commission’s Central Committee, sets the baton ready for warfare from the level of the Central Military Commission, and pays close attention to actual combat military training from the level of the chairman of the Central Military Commission. Grassroots officers and soldiers have no reason not to do a good job. We must unify our thoughts and actions to the important instructions of President Xi to prepare for war, and strive to forge an elite force that can be called, come to war, and win in battle.
Adhere to problem-oriented and make preparations for work
The great rejuvenation of the Chinese nation is by no means an easy task. It can be achieved by banging and playing drums. The ambitious goal of building a world-class army is also facing severe challenges.
Li Keliang, political commissar of a central information and communications brigade in the Central Theater, believes that we must strictly follow the requirements of Chairman Xi’s important directives, stick to the problem-oriented approach, grasp the end, and promote implementation of the preparations for combating one practical problem. It is necessary to establish a strict responsibility system, strengthen supervision and accountability, and grasp first-level, first-level and first-level levels, and stringently prepare for war preparations.
“The battlefield is a real contest, and the fight is a hard-fought duel.” The party’s 19th representative and Navy carrier-based fighter pilot Cao Jianjian created 419 days after serious injuries and only after 70 days of go-around, the F-15 fighters succeeded in their operations. The ship’s miracle, “In the past few years, the entire army took the training winds to test the wind and declared war on the “peace and evil” in military training. During the exercises, they dared to expose problems and dare to dissect themselves. They introduced a series of hard measures and effective. Promote the building of the combat effectiveness of the troops.”
After seriously studying Xi’s speech, a brigade commander of the 80th Armed Forces believed that we must follow the example of President Xi’s entrustment to strengthen the sense of crisis, awareness of crisis, and awareness of snoring. We must focus all our efforts on fighting and focus on each other’s work. We must make preparations as soon as possible. Snoring ability to engage in.
Experts and scholars of the Academy of Military Sciences, National Defense University, and National University of Defense Technology, according to the future situation and task, believe that we must use the important instructions given by President Xi’s visit to the joint operations command center of the Central Military Commission as guidelines, and focus on innovating wars and combat planning, closely following the evolution of war formations and combat methods. , Adhering to the combat missions, operational opponents, and operational environment, Daxing’s research on warfare issues.
President Xi’s strong mission, clear preparations for fighting, and inspiring the majority of officers and soldiers of the entire army and armed police forces. The officers and men said that we must firmly establish the only basic standard of combat effectiveness. All our thoughts must be focused and focused on. All tasks should be used to fight hard, and we must successfully accomplish the mission of the new era entrusted by the party and the people!
Original Mandarin Chinese:
习主席视察军委联合作战指挥中心在全军和武警部队引起强烈反响
全面提高新时代备战打仗能力,为实现中国梦提供战略支撑
“实现党在新时代的强军目标、把人民军队全面建成世界一流军队,必须扭住能打仗、打胜仗这个关键,在备战打仗上有一个大的加强。”3日,习近平主席视察军委联合作战指挥中心,带领军委一班人研究军委联指中心建设情况,同驻守边防海防的有关任务部队官兵通话,通过视频察看了驻吉布提保障基地,听取了全军练兵备战工作汇报,并发表重要讲话,在全军和武警部队引起强烈反响。
官兵们纷纷表示,这次视察充分体现了习主席对军队备战打仗问题的高度重视,表明了新一届军委贯彻落实党的十九大精神、推动全军各项工作向能打仗、打胜仗聚焦的鲜明态度。大家表示,一定要认真学习贯彻党的十九大精神,坚持以习近平强军思想为指导,贯彻新形势下军事战略方针,强化使命担当,强化改革创新,强化工作落实,全面提高新时代备战打仗能力,为实现“两个一百年”奋斗目标、实现中华民族伟大复兴的中国梦提供战略支撑。
时刻绷紧战备这根弦,强化备战打仗导向





3日上午,窗外寒气袭人,但军委联合作战指挥中心却暖意浓浓。习主席一身戎装来到军委联指中心大楼,带领军委一班人研究军委联指中心建设情况。
“习主席视察时发表重要讲话,深刻阐明全面提高新时代备战打仗能力的战略意义和实践要求。”亲历视察全过程的中央军委联合参谋部作战局副局长周尚平说,“这是党的领袖、我军统帅领航人民军队为实现党在新时代的强军目标、全面建成世界一流军队,向全军官兵发出的政治动员和时代号令。”
军队是要准备打仗的,人民军队担负新时代使命任务的根本着力点在于战斗力。
各战区、各军种、军委机关各部门的官兵们在学习讨论中认为,全军官兵只有时刻绷紧战备这根弦,强化备战打仗导向,始终聚焦备战打仗,不断提升打赢能力,才能有效塑造态势、管控危机、遏制战争、打赢战争。
“如果你想要和平,那就要做好打仗的准备。”党的十九大代表王金龙担任指导员的中部战区陆军某旅“大功三连”,战争年代打出了赫赫威名,新时期,连队常年担负旅应急战备值班任务,始终保持箭在弦上、引而待发的战备状态。他认为,邦境不安,忘战必危。世界上的事情总是那样,你准备不好,敌人就来了;你准备好了,敌人反而不敢来。战争与和平的辩证法告诉我们,能战方能止战,准备打才可能不必打,越不能打越可能挨打。
“要把‘战’字刻在心头,持续强化‘随时准备上战场’的责任意识,将练兵备战的职责深深刻入脑海、成为自觉行动。”陆军航空兵某旅旅长崔佳彬说,真正做到一旦有事能快速反应,坚决完成党中央、中央军委和习主席赋予的任务,坚决维护国家主权、安全、发展利益。
狠抓实战化军事训练,提高打赢本领
中国特色社会主义进入了新时代,国防和军队建设也进入了新时代。
官兵们认为,新时代要求军队必须具备新的能力,而要具备新的能力,就必须大抓实战化训练。
“习主席在视察军委联指中心时指出,要着力深化实战化军事训练,坚持仗怎么打兵就怎么练,打仗需要什么就苦练什么,把官兵积极性、主动性、创造性充分激发出来,在全军兴起大抓军事训练热潮。”党的十九大代表、空军航空兵某团团长刘锐说,“这一点令我印象最为深刻,军队只有狠抓实战化军事训练,提高打赢本领,才能担负起党和人民赋予的新时代使命任务。”
刘锐所在团是空军首支改装轰—6K的航空兵部队,是空军远程进攻作战的重要力量。党的十九大闭幕之后的这一段时间,他除了宣讲党的十九大精神,其他所有时间都铆在训练场。几天前,他组织实施了团队历史上最大规模的跨区域机动作战训练,从昼间到后半夜,从战斗起飞到超低空,从陆上到海上,一路走一路打,跨越多个陌生区域和多个机场,持续9个多小时,航程近5000公里……
南部战区陆军第74集团军某合成旅“黄草岭功臣连”目前正在苦练精兵,迎接即将到来的集团军年终考核。指导员陈骁文认为,习主席视察军委联指中心,从军委这一层把备战打仗的指挥棒立起来,从军委主席这一级亮明狠抓实战化军事训练,提高打赢本领的鲜明态度,我们基层官兵没有理由不做好。我们一定要把思想和行动统一到习主席备战打仗的重要指示上来,努力锻造召之即来、来之能战、战之必胜的精兵劲旅。
坚持问题导向,抓实备战工作
中华民族伟大复兴绝不是轻轻松松、敲锣打鼓就能实现的,建设世界一流军队的宏伟目标同样面临十分严峻的挑战。
中部战区某信息通信旅政委李克亮认为,我们要严格按照习主席重要指示要求,坚持问题导向,一抓到底,在解决一个一个实际问题中推动备战工作落实。要建立严格的责任制,强化督导问责,一级抓一级,一级带一级,把备战打仗工作严起来。
“战场是实打实的较量,打仗是硬碰硬的对决。”党的十九大代表、海军舰载战斗机飞行员曹先建创造了身负重伤419天后、术后复飞仅仅70天,驾驶歼—15战机成功着舰的奇迹,“这几年,全军大抓训风演风考风,向军事训练中的‘和平积弊’宣战,在演习中敢于暴露问题、敢于自我解剖,出台了一系列硬性措施,有效推进部队战斗力建设。”
第80集团军某旅官兵在认真学习习主席的讲话后认为,我们一定要按照习主席嘱托,强化忧患意识、危机意识、打仗意识,全部心思向打仗聚焦,各项工作向打仗用劲,尽快把备战打仗能力搞上去。
结合未来形势任务,军事科学院、国防大学、国防科技大学的专家学者认为,要以习主席视察军委联合作战指挥中心的重要指示为指引,着力创新战争和作战筹划,紧跟战争形态和作战方式演变,紧贴作战任务、作战对手、作战环境,大兴作战问题研究之风。
习主席强烈的使命担当,鲜明的备战打仗态度,鼓舞着全军和武警部队的广大官兵。官兵们表示,一定要牢固树立战斗力这个唯一的根本的标准,全部心思向打仗聚焦,各项工作向打仗用劲,圆满完成党和人民赋予的新时代使命任务!
Reference (1) Www.xinhuanet.com/2017-11/04/c_1121906230.htm
Reference (2) http://military.people.com.cn/n1/2017/1105/c1011-29627206.html