中國軍方解釋了美軍演習在網絡戰中的作用 ~ China Military Explains Role of US Military Theater Operations in Network War
Who is responsible for configuring the information resources owned by the United States? Who is responsible for assigning these resources to use the priority order? What measures have we taken to ensure that the Global Information Grid (GIG), the Independent Joint Service System, and the GCCs: Geographic Combatant Commanders (GCCs) and Global Network Associations (GCCs), which rely on information from them, Trojans (JTF-GNO: Joint Task Force-Global NetOps) security? In recent years, the entire network combat system on the discussion of these issues has not been suspended, the focus of debate is the theater operations in the network operations should play what role.
The US military has announced the deployment of the war command for each theater, and also announced that it would reduce military support in the cross-border areas. For each theater combat command, how to configure the information infrastructure to support the war in the theater has become very important. The enemy may be infiltrated into the critical network system area responsible for military power dispatch, which is often underestimated and even treated as an accident or incidental event, but these intrusion is virtually Made a connection request to block the normal operation of the commercial website, and even led to some of the military logistics business logistics company was marked as invalid. The theater warfare command should ensure that the information conditions of its zone are not affected by external invasions. Countless viruses are destroying the Internet, the Department of Defense system began to be attacked. It is now under discussion whether the Global Network Joint Task Force should be disconnected from the military network on the Internet, but the military is concerned that with the cooperation of commercial suppliers alone, the Department of Defense can not guarantee that all logistical support operations will continue without error To go on. Each theater combat command is not sure about the state of the theater itself, and they are skeptical about the security of the global information grid itself, and they are concerned about their ability to carry out the tasks assigned to it.
(STRATCOM) and the global network of joint contingents in the network operations in the dominant ideology of the impact of the theater operations headquarters of its command and control of the zone has a more global network of operations control institutions to strengthen the United States Strategic Command Weakened. The focus on the operational information grid to the global information grid has also affected, to a certain extent, the battlefield operations command of the global information grid is how to support the theater of the specific behavior of the understanding. This article will introduce the existing command relationship, the war between the theater operations command, the direct relationship between command and combat, the old and emerging joint operational principles of a special case analysis, and finally will be the theater combat command In the network operations should play the role of the proposed recommendations.
Network combat environment
The command and control in cyber warfare is a concept that appeared ten years ago, and its connotation has been evolving. Each of the relevant departments, the theater operations headquarters and the global network of joint contingents have carried out some organizational structure and work focus on the adjustment, but ultimately did not solve their respective roles should play this issue. To really understand why the role of theater warfare in cyber operations will be a problem, it is necessary to clarify the question: where is cyber warfare, what is real cyber warfare, and every What is the organizational structure and command and control structure of the department?
The first thing to explain is, what is the global information grid? According to the definition of Ministry of Defense No. 8100.1, it includes “global interconnection, terminal-to-terminal information transmission capability and joint processing capability.” Ability to collect, process, store, transmit and manage information according to the needs of warriors and policy makers ” This covers government and leased communications information systems and services, as well as other software, security and service support required for global information grids, as well as the Clinger- The National Security System, as defined in Section 5142 of the Cohen Act. According to this definition, the global information grid contains all levels of information systems from the Department of Defense and the national security system, from the tactical level to the strategic level, as well as the interconnected communication system.
Most of the discussion on the command and control of the Global Information Grid Network Operations Center focuses on the defense capabilities of the system, but the content of the network operations is far more than that. The tasks to be accomplished by the network operations include three: departmental management, Content management and network defense, whose purpose is to provide a lack of central support across the boundaries of strategic, tactical and operational concepts, and to support the Department of Defense’s full range of combat, intelligence and mission tasks.
1. Sector management is one of the specific tasks of the global information grid, which is the technology, process and policy management of systems and networks that make up the global information grid, including public sector management, systems management, network management, satellite communications management and Electromagnetic spectrum management of these aspects.
2. Content management refers to managing the information itself in the global information grid. It ensures that information is available to users, operators, and decision makers in real time. Content management includes the search, access, transmission, storage and integration of specific information content of the global information grid.
3. Network defense is the global information grid all the information, including additional information to protect, it mainly includes a number of policies, processes, projects and operations. If necessary, the task can be requested through cross-agency cooperation to complete. It is responsible for the global information grid information security, computer network defense, computer defense response capabilities and critical infrastructure protection.
Now we have learned about the basic organizational structure of the cyber warfare, the next step in the various organizations in the network operations and how they are performing the tasks, which are mainly composed of troops, theater warfare headquarters and global network joint contingents, all of which are With the changes in the battlefield requirements to improve their organizational structure.
The change in the organizational structure of the force is mainly to meet the requirements of the global information grid for information transmission, access, control and protection. Ten years ago, the troops had some changes to regional control in order to adapt to cyber warfare, but those measures eventually developed into centralized controls, and these measures were not preserved. Now it is necessary to understand the composition of the forces in order to better understand why the network operations command and control will become so full of controversy.

GEM: GIG Enterprise Management GCM: GIG Content Management GND: GIG network defense
Army ‘s network operations command and control
The army is the least of all the reforms in the service. The Army continues to hold the previous commander, now known as the Theater Network Operations and Security Centers (TNOSC), which is directly responsible for the various theater war operations. The Army maintains an independent global network operations and security center (GNOSC: Global NetOps and Security Center), all of the battlefield network operations and security centers are its affiliates. The Global Network Operations and Security Center has technical control over the Battlefield Network Operations and Security Center, but the Battlefield Operations and Security Center is also part of the Theater Command and is also managed by the Theater Network Command. A typical example is the Army’s battlefield signal The brigade is managed by the Army Service Component Command.
The Global Network Operations and Security Center provides technical guidance to the network operations forces in each theater. The US Army Network Command and the 9th Signal Command are responsible for the technical and management of the Global Network Operations and Security Center. But in wartime, the Global Network Operations and Security Center was also commanded by the Strategic Command (STRATCOM) as Army Element.

ACERT: Army Computer Emergency Response Unit
AGNOSC: Army Global Network and Security Center
ASCC: Army Army Command
ARSTRAT: Army Strategic Command (Missile Defense and Strategy)
CIO: Chief Information Officer
GCC: Theater Combat Command (Regional Joint Command, Six of the US Army’s Top Ten Command)
INSCOM: Intelligence and Security Command (one of the Army’s reporting units)
JTF-GNO: Joint Task Force – Global Network Operations Command
NETCOM: Army Network War Command
RCERT: Regional Computer Emergency Response Team
STRATCOM: US Strategic Command
TNCC: Theater Network Operations Control Center
TNOCC: Theater Network Operations and Security Center
G6: Army Command Department of Communications
G2 Army Command Information Department
Installation Network Provider
COMMAND – Strategic level operational command
OPCON: Battle (Battle) Command
TACON: tactical control
GS: Global Strike
TECHCON: echelon
ADCON: management control
Air Force ‘s Network Operations Command Control
The Air Force has chosen a different organizational approach to move the focus from the former headquarters of the Network Operations and Security Center (MAJCOM NOSCs) to the Integrated Network Operations and Security Centers (I-NOSCs: Integrated NetOps and Security Centers). Unlike the Army’s Battlefield Network Operations and Security Center, which is managed by the Theater Operations Command, the Air Force’s Integrated Network Operations and Security Center is not affiliated with any theater war command, but only by the Air Force Operations Center (AFNOC : Air Force NetOps Center), which is similar to the Army’s Global Network Operations and Security Center. The Air Force realizes that the Theater Command must have the power to direct direct operations in its zone, and it is necessary to establish a general support relationship between the Air Force Operations Center and the Theater Operations Command, establishing a dedicated link between the two departments unit. In addition, the Air Force has given a command to the establishment of a communications control center in their respective theater areas. These control centers can be used as a shortcut between the Air Force Operations Center and their respective theater operations.

ACC: Air Warfare Center
AFCHQ: Air Force Command
AFNETOPS: Air Force Network Operations Command
ARSTRAT: Air Force Strategic Command Theater Network Operations Control Center
CIO: Chief Information Officer
I-NOSC: Integrated Network Operations and Security Center
GCC: Ibid., Regional Joint Command
JFCC-NW: Network War Joint Function Composition Command
JTF-GNO: Ibid., Joint Task Force – Global Network Operations Command
NCC: Network Control Center
STRATCOM: Ibid., Strategic Command
TNOS: Ibid., Theater Network Operations and Security Center
Naval network operations command control
The Navy and the Air Force, no longer regard the theater as a unit of command. In order to better support global operations, they assisted two existing theater naval warfare centers (RNOSCs) affiliated with the Naval Global Network Operations and Security Center (NAVGNOSC) to assist the original two naval schools in Naples and Bahrain Communication master station (NCTMS: Navy Computer and Telecommunications Master Station). In addition, since most of the Navy’s cyber operations were carried out at sea, they also established Fleet NetOps Centers (FNOCs: Fleet NetOps Centers), echoing the theater and cyber warfare centers located in the United States. The fleet network operations center is the tactical entry point for the fleet to conduct cyber operations, providing network services for audio, video and data for the fleet of the zone, and can be provided when the fleet goes from another area of the fleet network operations center into another area Smooth information transitions. Most unclassified networks are contracted by the US Navy Marine Corps Internet or the US Overseas Overseas Navy Enterprise Network (ONENET: Outside of CONUS Navy Enterprise Network). In order to meet the needs of the battlefield, the Navy established the Overseas Marine Corps Intranet Global Network Operations and Security Center to provide global combat support, as well as the establishment of a war zone network combat and security center of the theater network security center on each Specific battlefield support. There is no subordinate relationship between the Theater Network Operations and Security Center and the theater operations headquarters in the theater.

Fleet NOC: Fleet Network Operations Center
GCC: Ibid., Regional Joint Command
INSCON: Ibid., Army Intelligence and Security Command
JTF-GNO: Ibid., Joint Task Force – Global Network Operations Command
NAVGNOSC: Navy Global Network Operations and Security Center
NAVSOC: Navy Satellite Operations Center
NCC MHQ: Navy Network Operations Information Operations and Space Warfare Center
NMCI GNOC: Maritime Network Global Network Operations Center
RNOSC: ibid, regional network operations center
STRATCOM: Ibid., Strategic Command
TNCC: Ibid., Theater Network Operations Control Center
Navy Global Network Operations and Security Center (NAVGNOSC) and the East and West Regional Network Operations and Security Center (East and West RNOSCs), which support the most basic organization of global naval operations. The Naval Global Network Operations and Security Center brings together information from the Theater Network Operations and Security Center, the Overseas Marine Corps Intranet and the Naval Satellite Operations Center to provide global command and control information for the Global Network Operations Joint Task Force. Unlike the Navy and the Army, they did not maintain a body belonging to the Theater Command. The support relationship between the forces established by the Joint Operations Task Force of the Global Network Operations and the Theater Warfare Command did not give the theater war command the power to command the Naval Department’s global information grid. All command requests of the Theater Warfare Command must be approved by the Navy’s Global Network Operations and Security Center.
Command and Control of Theater Combat Command
Although each theater combat command in their respective jurisdictions for network operations are not the same way, but they have a common feature, that is, have established a theater network operations control center and a subordinate to the defense information system (DISA: Defense Information Systems Agency) of the theater network operations center. (CENTCOM) will be the theater network operations control center and the Defense Information Systems Agency’s theater network operations center known as the Central Theater Network Operations Center (Central Region Theater NetOps), the Central Commander of the Central Theater, Center, and the European Command (EUCOM) has established a Theater Communication Control Center (Theater Communication Control Center). Although there are some differences in the organization, but all the theater network operations control center are basically used by the theater combat command for the area of the global information grid command control (area of the global information grid is also known as the theater Information Grid TIG: Theater Information Grid).
The Theater Operations Command has optimized the configuration and control of the information resources of the global information grid through the Theater Network Operations Control Center to enable them to better serve the battle, while the Theater Network Operations Control Center is also connected to the Defense Information Systems Authority, the regular forces and the global Joint Operations of the Network Operations Joint Task Force. They collaborated with the Theater Network Warfare Center, the Theater Network Operations and Security Center to monitor the status of the theater information grid, to decide on the proposed global operations of the Joint Operations Task Force, and to assess the impact of its actions. The Theater Network Warfare Control Center has the right to decide on the reduction and termination of combat operations and to adjust the priority of operations through the Theater Network Operations Center and the Theater Network Operations and Security Center. If there is no theater network operations and security center in the theater, the theater network operations control center under the Global Network Operations and Security Center tie is responsible for completing the mission required by the Theater Operations Command.
The North North Command (NORTHCOM) is a rather special sector, although it is a theater warfare command with a clear zone, but most of its troops in the zone – including cyber combat troops – are not affiliated with the commander , But belong to the United States Joint Forces Command (JFCOM: Join Forces Command). This deployment is intended to facilitate the global management of the force. The North Command, like several other theater warfare commanders, also set up a theater network operations control center, but did not establish a theater network operations and security center, which makes the North Command must rely on network operations and security centers and other departments for its Provide general support. In this case, the role of the North Command is to be responsible for the operations within its jurisdiction, but also the lack of understanding of the corresponding battlefield information grid, and no direct control of its power.
Strategic Command Network Operations Command Control
With the troops fighting command on the network combat structure to adjust the same, the Ministry of Defense departments are also undergoing reform. Over the years, the Department of Defense has not had a centralized control of the network operations. But in 1997 when the Department of Defense conducted this attempt to find some of the weaknesses of the network at that time, also came to the “combat command – troops – defense agencies,” this network mode of operation is not suitable for modern battlefield situation The That attempt has led to the formation of a Defense Force (IAA) bureau, which is part of today’s Global Network Operations Joint Task Force, which is responsible for the operation and defense of global information grids.
Global Network Operations Joint Task Force network operations command and control mechanism is also constantly evolving. Prior to the advent of the existing UCP: Unified Command Plan, the command and control of the Global Network Operations Joint Task Force was under the responsibility of the Theater Operations Command, but it proved that it was not conducive to managing all the components in the network, It is also difficult to provide enough information for the global information grid information. The original version of the operational concept of cyber warfare emphasizes the control of the theater operations of the theater in the theater, which was described as follows: “The combat command has the power to command the troops assigned to its zone, Is conducive to the completion of the task, when the combat command feel appropriate, or even adjust the priority of the global information grid.All of these activities should be through the theater network operations center to achieve. “In fact, even the global Event, the initial version of the network combat concept document also provides that the global network operations Joint Task Force needs to be in the theater combat command of the theater network operations control center under the command of combat.

The follow-up version of the operational concept has been adapted to this principle. The control of the Global Network Operations Joint Task Force was moved to a more global command and control structure, through which the overall role of the strategic headquarters, the Global Network Operations Joint Task Force and other forces involved in the network operations Has been strengthened. The operational concept of the Global Network Operations Joint Task Force is subdivided into three environmental operational concepts: global, theater and non-global. What kind of environmental concepts apply to different events depends on the actual impact of the events and the impact of the theater. This form of command and control structure is more suitable for the current network combat diversity characteristics, for different levels of events, theater combat command can take a more flexible response measures, and even at the same time to support and supportive action. In this system, sometimes the process of dealing with the event to go through a complete command system chain, and sometimes you can skip some steps.
Global events
Global events refer to activities or events that clearly affect the preparedness of the entire global information grid, which often requires the concordation of multiple theater combatants to be resolved. Commander of the Strategic Command must have the ability to quickly identify global events and to be able to determine which theater combat operations or other agencies of the Department of Defense will be affected. Global events include fast-spreading network malicious code attacks, satellite communications attacks, and enterprise application attacks that are not limited to single-theater network events.
The Global Strategic Command is a reliable command center with command and command for the Global Network Operations Joint Task Force and the Theater Command. The Global Network Operations Joint Task Force uses its own resources to execute the instructions of the Strategic Command, which can be quickly sent to troops around the world. It is noteworthy that this order is not in the event of transmission to the theater of combat operations.
Although the notion of operational concept conferred the command of the commander of the strategic command worldwide, it did not completely deny the right of the theater war command to be commanded by the assigned joint command. While the Global Network Operations Joint Task Force performs the operational command of the Strategic Command, the Theater Operations Command can also deploy its troops to carry out the corresponding activities. Of course, in accordance with the requirements of the operational concept, the forces under the leadership of the theater operations command must be consistent with the action guidelines of the Joint Operations Task Force under the leadership of the Strategic Command. In fact, according to the historical action log of the Joint Operations Task Force of the Global Network Operations, most of the cyber operations began at the beginning of a small theater, and the Theater Command was always the first unit to deal with these incidents, and If they are handled properly, these theater-level events will not develop into global events.
Theater events
Theater events are those that occur in a battlefield area, and its foreseeable range of influence does not go beyond the theater, and the biggest difference between theater and global events is that. In the event of such incidents, the theater operations headquarters played a leading role, while the strategic headquarters only take the support role. The Global Network Operations Joint Task Force can provide support to the Theater Command by its Theater Network Operations and Security Center. If the local forces do not have a theater network operations and security center, it can also provide general support for the Theater Network Operations Control Center through the Global Network Operations and Security Center. The Command of the Theater Combat Command to the Global Network Operations Joint Task Force is subordinate to the subordinate command, that is to say there is no right to direct the Global Network Operations Joint Task Force through its Global Network Operations and Security Center to operate in its area.
Non-global event
A non-global event is an event that only affects the functional warfare headquarters and a particular defense agency. Since such institutions do not have a clear zone, these events can neither be regarded as global nor can they be seen as theater. In dealing with non-global events, the Strategic Command plays the role of auxiliary command, and the Global Network Operations Joint Task Force provides general support for the operational operational warfare headquarters involved. Most of the non-global events generally occur in the northern command zone, since many of the relevant functional departments are subordinate to the Northern Command. In the case of command and control procedures, non-global events and global events are the same.
Contradictory command and control requirements
Tactical technical requirements
Although the positioning of the various forces are not the same, but in the pursuit of efficient network operations, reasonable combat methods are their common theme. Different forces shoulder different responsibilities, they established an independent combat network, application facilities and auxiliary tools to meet their own and global information grid to maintain connectivity needs. Each unit is responsible for operating part of the global information grid, which to some extent the need for combat operations between the various departments of the centralized management, so as to get the desired combat efficiency and return on investment.
The focus of the discussion on centralized control of global information grids is the global nature of cyber warfare. The only way for the Department of Defense to achieve a network-centric commanding mechanism, to enhance the Force’s awareness of the situation and to significantly shorten the decision-making cycle, is to integrate the network and the forces horizontally, which is a centralized control mechanism The The latest “four-year defense assessment report” mentioned in the “to simplify the current ‘chimney’ system structure, to achieve a network-centric command mechanism.”
In order to make better use of scarce resources, the Department of Defense must consider when and where to allocate resources from a global perspective. The allocation of essential resources for network operations such as satellite transmission bands, standard tactical entry network sites and bandwidth must have clear mission objectives and easy to understand global significance. From the perspective of the force, the centralized command is, to some extent, a reshuffle of the existing force institutions and operations, defense networks.
The combat operations led by the theater war command will no longer be strictly limited to its zone. Ground forces are re-starting to use aircraft (including unmanned aerial vehicles) to routinely fly in the United States to support their operations. With the development of the PGS: Prompt Global Strike project, the commander has the power to call for conventional strike assistance from weapons systems outside the theater.
On the Navy, they pointed out that one of the essential characteristics of the maritime forces was global mobility, and the naval forces were constantly interspersed between the various theater warheads. Especially as aircraft carrier battle group such units, once deployed, it can not stay in a small battlefield. In addition, even the theater-level operations taken by the theater war command may have a global impact. The adjustment of the network defensive posture may have a huge financial burden on the Internet sector, and the combat command may not be able to understand the specific details of the adjustment behavior.
For the Department of Defense’s network system, all attacks are essentially global in nature. The enemy can not easily from the other side of the Earth to the United States to attack the physical objectives, but in the field of computer network technology, such things happen often. Once such an attack is detected, the information about it must be communicated to all relevant departments in the shortest possible time to ensure that such attacks are identified from anywhere to protect the security of the global information grid. Every time a network intrusion – even if it does not seem to fail the invasion – is likely to give the global information grid content a huge potential harm, because they invade the system behind the back door will be in the future Attack to play a role. The outbreak of the virus is an undisputed global event, and if we do not realize this, we will suffer more losses.
The Navy emphasizes that the impact of no events will be limited to a theater area, and that all efforts to combat cyber operations must be global. Their defense is that there is no theater boundaries, the Department of Defense every battlefield combat headquarters are facing the same potential threat, in order to obtain information on the advantages of the Department of Defense must make full use of its large coverage of the network resources , Quickly share all useful information on a global basis.
In addition, the Air Force and the Navy have pointed out that their cyber warfare forces are not deployed by the Theater Warfare Command. The Air Force and the Navy have their own cyber warfare organizations (such as the Theater Network Operations and Security Center) in each zone of the Theater Command, and the Air Force and Navy’s cyber warfare forces are usually defender in the theater. Finally, the Air Force and the Navy believe that the Strategic Command is responsible for the Global Information Grid through the Theater Operations Command, based on the description of the official documents available for reference.
Theater war command
There are two issues that need to be concerned about the command and control of cyber warfare against the Theater Command. One is the need for timely control of the battlefield information grid, the second is the need to turn the network into a weapon system, so that commanders can be the same as the conventional weapon system to use the same network resources, the use of the full range of network advantages to conduct a comprehensive battle.
Those forces that have been assigned specific responsibilities have already deployed their own unique solutions, each of which is involved in a network operation or each institution believes that it already has the most effective allocation of scarce resources. But the global information grid is not exclusive to a particular department, but a joint structure. “Chimney” type system and the existing deployment of the troops is actually to reduce the efficiency of the battlefield information grid efficiency. For example, the Army developed a secure IP telephony solution before other departments in the Department of Defense to communicate with the secret voice. For security reasons, other departments usually do not use this program, but their own development of a set of the same function of the solution. So there will be two sets of independent, confidential IP voice schemes in the zone of the Combat Command, which can not be connected to each other. The theater warfare command had to be screened, leaving only a set of programs to ensure that all departments in their zones could cooperate with each other. But the solution is eliminated by the party can no longer with the theater outside the brother forces for confidential contact.
Some of the resources in the combat command zone can serve multiple forces and the public sector. However, there are many examples of the use of duplication of work for the establishment of their own can not be linked to each other independent systems, such as satellite terminals and some technical control equipment. Sometimes, to send a message, you need to send the signal back to the United States, and then sent from the local distance from the initial sender only two miles of the recipient there. All kinds of fibers are arranged one by one on the same route, but the data between them can not be exchanged directly because they belong to different forces or public departments. The theater operations command must take measures to address the interconnection between the troops or the civil service in the zone.
To solve this problem, you can use centralized control approach. The centralized command of the cyber warfare forces requires the theater war command to make some adjustments to its own organization, but at the same time it does not affect its power to direct action when there is a need for combat. Relevant forces must accept orders for multiple combat orders and effectively optimize and feedback battlefield information. At present, the troops sent to the front are becoming more and more independent, and through the help of the global information grid they can cross the border of the theater combat command back and forth, and the theater warfare command has been compromised by the support and confrontation of the cyber warfare , After the implementation of centralized command, the troops can not or do not want to respond to the requirements of the theater combat command.
The Pacific Command (PACOM: Pacific Command) first adopted a “joint attempt” approach in humanitarian aid operations when it participated in the Indonesian tsunami relief work in 2004. The Pacific Command issued instructions to the assigned troops to carry out special network defenses under the framework of the entire action plan. Many naval forces and Marine Corps units have established relatively direct network defenses under the centralized command of the Navy’s Global Network Operations Center, which goes beyond the mandate of the Pacific Command to the Navy and Marine Corps, which Posing a potential risk factor for the global operations of the Pacific Command.
The Combat Command is concerned that the idea of centralizing control of global information grids will always reduce their grip on information and control of the global information grid. Under the existing command system, a unit will carry out training or perform other tasks under the command of its troops, and participate in the battle under the command of the theater combat command, and the rules of command and control are very clear. The command and control of the forces in the field of information is as important as their command and control in the air, land, sea and space fields. For the C3S system (control, communications and computer systems), under its command to combat and responsible for the protection of its forces are often in a double or even triple the report chain, the results can not tell who is responsible for the final battle. In a global or non-global event, the Global Network Operations Joint Task Force often conducts direct operations around the theater operations headquarters. Although the operational concept of joint cyber warfare specifically emphasizes the need for coordinated operations with the theater combat command, this requirement has become almost in the context of modern combat rapid changes. Information Security Weakness Alert System, Computer Task Sequence, and Information Condition Adjustment System Problems outside the jurisdiction of the Combat Command are typical examples of this requirement failure. These events directly affect the command of the Theater Command in the battlefield, when the troops want to directly use these mechanisms from the management level to strengthen their own control, they can not determine when and how in the implementation of these Operation, and do not know what impact this will have on the command of the theater combat command, because under current conditions, only the theater combat command has the ability to carry out these operations. When a threat event requires the Air Force’s Space Command to seek the cooperation of the Joint Operations Task Force of the Global Network Operations with Air Force forces, it would bring to the command of the North Command if it did not notify or obtain cooperation with the Northern Command Big trouble.
In the Central Command, due to the lack of adequate control of the network combat forces, resulting in the commander sometimes can not determine whether the network resources are available. The Navy is responsible for operating a large number of battlefield information grids. Navy network combat forces in the operational area are not responsible for the Central Command of the Navy, who only need to report to the Theater Network Operations and Security Center. The central theater’s central theater theater operations center, whose duty is to maintain and direct all the combat operations of the theater operations, but it is not in the naval network combat force report chain, so it is often impossible to get all the battlefield information grid Of the state of affairs, there are already alternatives to deal with this problem, but this can not be said to be a formal solution.
For the North Command, because of the lack of cyber warfare control, they encountered great trouble in the rescue work of Hurricane Katrina in 2005. In that operation, the troops’ equipment was transported to the joint warfare zone without permission. Which makes the North Command can not grasp and guide the transfer of materials, but can not coordinate the actions of various forces, which is a multi-directional management and operational issues.
As the various forces advocate the implementation of a centralized command framework centered on the Global Network Operations Joint Task Force, it is necessary to emphasize the fact that the theater commanders are reluctant to see such changes, Some of them are responsible for the strategic headquarters, with the global information grid operating rights and defense rights mechanism. The presence of the Strategic Command has been instrumental in maintaining the command of the theater combat command in combat operations in theater and global events and in enhancing communication between the theater combat command and the Joint Staff.
Combat headquarters and troops want to focus on the network operations from the level of joint operations, but there are several issues that need to be discussed:
Who is responsible for the first leadership?
2. Network operations to focus on what the specific direction of the command to be reflected, the global level, the theater level or what other level?
3. What is the change brought about by this adjustment only when a part of the theater combat command sends a request to the Global Network Operations Joint Task Force or is the theater commander’s complete command and priority in the theater?
Finally, the Theater Command is the body that is ultimately responsible for the President’s mission to complete the military mission in the area, and the troops dispatched to the theater combat command need to complete their respective tasks under their jurisdiction. It is unquestionable that they will still be under the command of the strategic command when the troops advocate the implementation of a global centralized command. But the current global information grid is a key part of the command and control capability of the theater combat command and the commander’s ability to guide the troops. Without a global information grid, the plane can not fly, the ground forces can not move, the ships can not sail, even the satellite can not provide the signal. Commanders need to get the status of the global information grid and control, just as they need to master the position and status of the troops as important. They must grasp the scope, ability and status of the battlefield information grid, and must know how the situation outside the theater will affect the battlefield information grid in the area where the troops are located and must be able to command and optimize the troops to support operations. If we really believe that the speculation of the centralized command will have a better effect, it can not be ignored for the theater war command to retain the appropriate command and control.
Also, as long as the structure of the Theater Command is still preserved, all military missions, including those directed by the Functional Command Command, will inevitably occur in the theater of the Theater Command, as all networks Combat missions must be carried out by an entity unit. At the same time, centralized command is necessary to achieve a network-centric command model and to more effectively defend against attacks. The concept of this centralized command and the command of the theater war command to master and optimize the battlefield information grid is not mutually exclusive.
The way forward
To develop a viable network combat command and control framework, it is necessary to avoid extremes, taking into account the needs of theater warfare headquarters and the need to establish centralized control of global information grids. In the process of the development of the operational concept of joint network operations and the transformation process of network combat forces, the principle of organization needs to play the role of adjusting the interests of all parties. In order to achieve this goal, the Department of Defense should do the following:
1. Create a simple, clear network combat command chain, to ensure that the strategic headquarters of all network operations can be directed. This can solve the problem just mentioned “who is responsible for the first leadership”. Only when the event occurred in a rapidly changing environment, the theater command and control agencies began to play a role. Simple command chain can ensure that troops involved in network operations know who should listen to who should report to whom, in this command chain, must include the theater combat command.
2. The command of the theater war command in its zone can be given:
– to amend the Joint Command plan to clarify the responsibilities of the Theater Operations Command to operate the network in its zone.
– Revise the existing global information grid network operational concept, detailing that those outside the theater network operations and security centers can obtain direct assistance from the World Network Operations and Security Center of the Theater Operations Command.
– All orders for the Global Network Operations Joint Task Force shall be enforced through the Theater Operations Command.
These adjustments ensure that all units in the theater are acting under a single command chain, which is responsible for the strategic headquarters through the Theater Operations Command. This can also solve the North Command should be responsible for the area but did not command the power of the network fighting the embarrassing situation.
3. In each theater combat command, a joint network operations center under the jurisdiction of the Central Command shall be established to integrate the Theater Network Operations Control Center of the Theater Command Command and the Theater Network Operations Center of the Global Network Operations Joint Task Force. As a result, each theater war command will have a joint operations command in the field of computer space, just as in the battlefield of land, sea and air. Any troops outside the Theater Network Operations and Security Center can obtain direct assistance from the Global Network Operations and Security Center of the Joint Network Operations Center.
4. To consolidate the status of the global information grid, the highest control to the strategic headquarters. The development of centralized command is now focused on the command of the forces involved in the network operations, which runs counter to the network-centric command concept. The force-centric “chimney” command system is not conducive to the transmission and processing of information, let us from the “all users to provide the latest and most accurate information” goal farther and farther. In the previous “Goldwater Nichols Defense Ministry Reconstruction Law” report has made it clear that the organization and management and command and control should be controlled by a joint agency.
Concluding remarks
The current centralized command of network operations is an urgent need. Optimizing the network operational command mechanism can help the Department of Defense to improve efficiency, save costs and better allocate scarce resources. More importantly, this allows network combat troops to provide information more quickly and accurately to commanders, which is important in large-scale network operations. The process of centralized command can not affect the efficiency of network combat command and control. This depends on whether the global information grid can provide enough information for all participating units and whether the commander makes full use of the theater information grid to help command operations.
“We have to change the network combat problem discussion and thinking mode, we are in the network” combat “rather than the network” management “, all participating units must ensure that they are ready to war every time to ensure that the network system A decisive weapon system. ” Network operations are a key part of our country’s ability to win war, it can help us provide command and control, shorten the decision-making cycle and adjust the resources of the theater. The Strategic Command has taken a big step in strengthening the concept of cyber warfare, and these efforts need to be continued. The theater warfare command must be an important part of the control and protection of the global information grid to ensure that we can continue to win the network.
Original Mandarin Chinese:
是誰在負責配置美國所擁有的信息資源?誰在負責分配這些資源利用時的優先級順序?我們採取了哪些措施來保證全球信息柵格(GIG:Global Information Grid)、獨立聯合服務系統以及依靠從它們身上獲取信息來開展工作的戰區作戰司令部(GCCs:Geographic Combatant Commanders)和全球網絡聯合特遣部隊(JTF-GNO:Joint Task Force-Global NetOps)的安全?最近幾年以來,整個網絡作戰系統對這些問題的討論一直沒有停息過,人們爭論的焦點就是戰區作戰司令部在網絡作戰中應該扮演什麼樣的角色。
美國軍方公佈了對每個戰區作戰司令部的部署,同時還宣布將會減少跨戰區的軍事支持行動。對每個戰區作戰司令部來說,如何配置支持本戰區作戰的信息基礎設施就變得非常重要了。敵人有可能會滲透進負責軍事力量調度的關鍵網絡系統區域進行破壞,這些入侵的危害常常被低估,甚至被當作意外事件或者偶發事件輕描淡寫地處理掉,但是這些入侵行為實際上完全有可能濫發連接請求來阻塞商業網站的正常運行,甚至導致一些承擔軍隊後勤業務的物流公司被標為無效狀態。戰區作戰司令部應該保證其防區的信息條件不受外部入侵的影響。不計其數的病毒正在破壞著互聯網,國防部的系統也開始遭到攻擊。現在有人在討論是否應該讓全球網絡聯合特遣隊斷開互聯網上的軍事入網點,但軍方又擔心僅靠和商業供應商的合作,國防部不能保證所有的後勤支持行動都能繼續無差錯地進行下去。每個戰區作戰司令部對各自的戰區網絡狀態都不太確定,他們對全球信息柵格本身的安全持有懷疑態度,他們擔心其是否有能力執行分配給它的任務。
受到建立一個更全球化的網絡作戰控制機構、加強美國戰略司令部(STRATCOM)和全球網絡聯合特遣隊在網絡作戰中的主導地位思想的影響,戰區作戰司令部對其防區的指揮控制權有所削弱。將作戰信息集中到全球信息柵格的做法也在一定程度上影響了戰區作戰司令部對全球信息柵格是如何支持該戰區的作戰的具體行為的了解。本文將會介紹現有的指揮關係、戰區作戰司令部的職責、指揮和作戰之間的線性關係、舊有的和新興的聯合作戰原則一級特殊戰例分析,最後還將會對戰區作戰司令部在網絡作戰中所應扮演的角色提出建議。
網絡作戰的環境
網絡作戰中的指揮控制是一個在十年以前就出現了的概念,之後它的內涵一直處在演變之中。每個相關部門、戰區作戰司令部和全球網絡聯合特遣隊都為此進行過一些組織結構和工作重心上的調整,但是最終都沒有解決好各自應該扮演的角色這個問題。要想真正明白為什麼戰區作戰司令部在網絡作戰中的角色會成為一個難題,就必須先弄清楚這幾個問題:網絡作戰是在哪兒發生的、什麼是真正的網絡作戰、網絡作戰中的每個部門的組織結構和指揮控制結構是怎樣的。
首先需要解釋的是,什麼是全球信息柵格?按照國防部第8100.1號文件的定義,它包括“全球互聯的、終端到終端的信息傳輸能力和聯合處理能力。按照戰士、決策者的需要來進行信息採集、處理、儲存、傳播和管理的能力”。這就涵蓋了政府的和租用的通信信息系統及服務,以及全球信息柵格所需的其他軟件、安全和服務支持,還包括1996年3月頒布的《克林格-科恩法》(Clinger- Cohen Act)第5142節所定義的國家安全系統(National Security System)。按照這個定義,全球信息柵格包含了國防部和國家安全系統的所有級別的信息系統,從戰術層次到戰略層次,以及互聯通信系統。
大多數關於全球信息柵格網絡作戰中心的指揮控制的討論都在著重強調該系統的防禦能力,但是網絡作戰包含的內容其實遠不止這點,網絡作戰要完成的任務包括三項:部門管理、內容管理和網絡防禦,其工作目的是提供跨越戰略、戰術和作戰概念邊界的無中心式支持,為國防部的全方位的戰鬥、情報和考察任務提供支持。
1.部門管理是全球信息柵格的具體任務之一,它是對構成全球信息柵格的系統和網絡的技術、過程和政策管理,包括公務部門管理、系統管理、網絡管理、衛星通信管理和電磁光譜管理這幾個方面。
2.內容管理指的是管理全球信息柵格里的信息本身。它用即時的方式保證信息對使用者、操作者和決策者都是可用的。內容管理包括對全球信息柵格的具體信息內容的查找、訪問、傳輸、儲存和一體化。
3.網絡防禦就是對全球信息柵格所有的信息包括附加信息進行保護,它主要包括一些政策、過程、項目和操作。如果有必要的話,該任務可以請求通過跨機構合作來完成。它負責的是全球信息柵格的信息安全、計算機網絡防禦、計算機防衛反應能力和關鍵性基礎設施保護。
現在已經了解了網絡作戰的基本組織結構,下一步介紹網絡作戰中的各個組織和他們是如何執行任務的,需要介紹的主要是部隊、戰區作戰司令部和全球網絡聯合特遣隊,它們都在隨著戰場要求的變化而改進著各自的組織結構。
部隊在組織結構上的改變主要是為了滿足全球信息柵格對信息傳輸、訪問、控制和保護能力的要求。十年之前,部隊為了適應網絡作戰曾針對區域控制進行過一些變革,但那些措施最終發展成了集中化的控制,這些措施也沒有保留下來。現在我們有必要了解一下部隊的組織構成,以便更好地理解為什麼網絡作戰的指揮控制會變得如此充滿爭議。
GEM:GIG企業管理 GCM:GIG內容管理 GND:GIG網絡防禦
陸軍的網絡作戰指揮控制
陸軍是所有軍種中改革措施最少的。陸軍繼續保持著以前的指揮機構,現在叫做戰場網絡作戰與安全中心(TNOSC:Theater NetOps and Security Centers),該組織直接對各個戰區作戰司令部負責。陸軍維持著一個獨立的全球網絡作戰與安全中心(GNOSC:Global NetOps and Security Center),所有的戰場網絡作戰與安全中心都是其下屬機構。全球網絡作戰與安全中心對戰場網絡作戰與安全中心進行技術控制,但是戰場網絡作戰與安全中心同時又隸屬於戰區作戰司令部,也受到戰區網絡司令部的管理,典型的例子就是陸軍的戰場信號旅受陸軍服務組件指揮部的管理。
全球網絡作戰與安全中心對各個戰區的網絡作戰部隊提供技術指導。美國陸軍網絡司令部暨第9信號司令部對全球網絡作戰與安全中心的技術和管理負責。但是在戰時,全球網絡作戰與安全中心又作為陸軍的元素受戰略司令部(STRATCOM)的指揮。
ACERT:陸軍計算機應急響應分隊
AGNOSC:陸軍全球網絡和安全中心
ASCC:陸軍軍種組成司令部
ARSTRAT:陸軍戰略司令部(導彈防禦與戰略)
CIO:首席信息官
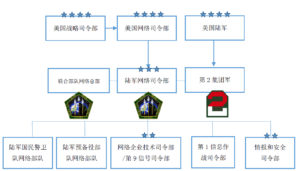
GCC:戰區作戰司令部(地區性聯合司令部,美軍十大司令部中的六個)
INSCOM:情報和安全司令部(陸軍直屬報告單位之一)
JTF-GNO:聯合特遣部隊-全球網絡作戰司令部
NETCOM:陸軍網絡戰爭司令部
RCERT:地區性計算機應急響應分隊
STRATCOM:美軍戰略司令部
TNCC:戰區網絡作戰控制中心
TNOCC:戰區網絡作戰和安全中心
G6:陸軍司令部通信部門
G2陸軍司令部情報部門
Installation Network Provider網絡施設提供商
COMMAND—戰略層面作戰指揮
OPCON:作戰(戰役)指揮
TACON:戰術控制
GS:全球打擊
TECHCON:梯隊
ADCON:管理控制
空軍的網絡作戰指揮控制
空軍選擇了一條不同的組織途徑,把重點從以前的一級司令部網絡作戰和安全中心(MAJCOM NOSCs)轉移到了一體化網絡作戰和安全中心(I-NOSCs:Integrated NetOps and Security Centers)。與陸軍的戰場網絡作戰與安全中心受戰區作戰司令部的管理不同的是,空軍的一體化網絡作戰和安全中心並不隸屬於任何一個戰區作戰司令部,而是只受空軍網絡作戰中心(AFNOC :Air Force NetOps Center)的管理,該中心與陸軍的全球網絡作戰和安全中心性質類似。空軍意識到了戰區作戰司令部必須擁有在其防區直接指揮網絡作戰行動的權力,有必要在空軍網絡作戰中心和戰區作戰司令部之間建立起一般支持的關係,建立兩個部門之間的專用聯絡單元。另外空軍方面還賦予了一級司令部在各自的戰區建立通信控制中心的自主權,這些控制中心可以當作空軍網絡作戰中心與各自戰區作戰司令部相互聯繫的快捷通道。
ACC:空戰中心
AFCHQ:空軍組成司令部
AFNETOPS:空軍網絡作戰司令部
ARSTRAT:空軍戰略司令部戰區網絡作戰控制中心
CIO:首席信息官
I-NOSC:集成網絡作戰和安全中心
GCC:同上,地區性聯合司令部
JFCC-NW:網絡戰聯合職能組成司令部
JTF-GNO:同上,聯合特遣部隊-全球網絡作戰司令部
NCC:網絡控制中心
STRATCOM:同上,戰略司令部
TNOS:同上,戰區網絡作戰與安全中心
海軍的網絡作戰指揮控制
海軍和空軍一樣,不再把戰區當作指揮的單位。為了更好地支持全球作戰,他們用隸屬於海軍全球網絡作戰與安全中心(NAVGNOSC)的兩個戰區網絡戰安全中心(RNOSCs)來協助原有的位於那不勒斯和巴林島的兩個戰區海軍計算機與通信主站(NCTMS:Navy Computer and Telecommunications Master Station)。另外,由於海軍的大多數網絡作戰是在海上進行,所以他們還建立了艦隊網絡作戰中心(FNOCs:Fleet NetOps Centers),與位於美國本土的戰區網絡戰安全中心互為呼應。艦隊網絡作戰中心是艦隊進行網絡作戰的戰術切入點,可以為本防區的艦隊提供音頻、視頻和數據等網絡服務,並且可以在艦隊從一個艦隊網絡作戰中心的轄區駛入另一個轄區的時候提供平滑的信息過渡。多數未分類的網絡都是由美國本土的海軍陸戰隊內聯網(NMCI:Navy Marine Corps Internet)或者美國海外的海外海軍企業網絡(ONENET:Outside of CONUS Navy Enterprise Network)負責承包運營的。為了適應戰場的需求,海軍建立了海外海軍陸戰隊內聯網全球網絡作戰與安全中心來提供全球性的作戰支持,同時也建立了隸屬於戰區網絡作戰與安全中心的戰區網絡戰安全中心對各個具體戰場提供支持。戰區網絡作戰與安全中心與所在戰區的戰區作戰司令部並沒有從屬關係。
Fleet NOC:艦隊網絡作戰中心
GCC:同上,地區性聯合司令部
INSCON:同上,陸軍情報和安全司令部
JTF-GNO:同上,聯合特遣部隊-全球網絡作戰司令部
NAVGNOSC:海軍全球網絡作戰和安全中心
NAVSOC:海軍衛星作戰中心
NCC MHQ:海軍網絡作戰信息作戰和太空戰中心
NMCI GNOC:海軍陸戰隊網全球網絡作戰中心
RNOSC:同上,地區性網絡作戰中心
STRATCOM:同上,戰略司令部
TNCC:同上,戰區網絡作戰控制中心
支持全球海軍作戰的最基本的組織的海軍全球網絡作戰與安全中心(NAVGNOSC)和東西部戰區網絡作戰與安全中心(East and West RNOSCs)。海軍全球網絡作戰與安全中心匯集了來自戰區網絡作戰與安全中心、海外海軍陸戰隊內聯網和海軍衛星作戰中心的信息,為全球網絡行動聯合特遣部隊提供全球性的指揮控制信息。海軍和陸軍不同的是,他們沒有維持一個隸屬於戰區作戰司令部的機構。全球網絡作戰聯合特遣部隊建立的部隊與戰區作戰司令部之間的支持關係並沒有賦予戰區作戰司令部在海軍部負責的全球信息柵格範圍內進行指揮的權力。戰區作戰司令部的所有指揮請求都必須先經過海軍全球網絡作戰與安全中心的批准。
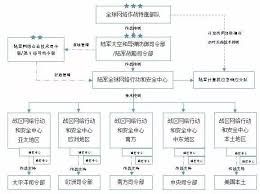
戰區作戰司令部的網絡作戰指揮控制
儘管每個戰區作戰司令部在各自的轄區內針對網絡作戰的組織方式都不盡相同,但是他們卻有一個共同的特點,那就是都建立了一個戰區網絡作戰控制中心和一個隸屬於國防信息系統局(DISA:Defense Information Systems Agency)的戰區網絡作戰中心。各個戰區網絡作戰控制中心的組織結構並不完全相同,美國中央司令部(CENTCOM)將戰區網絡作戰控制中心和國防信息系統局的戰區網絡作戰中心合稱為中央戰區網絡作戰中心(Central Region Theater NetOps Center),而歐洲司令部(EUCOM)則建立了一個戰區通信控制中心(Theater Communication Control Center)。雖然在組織上有些差異,但是所有的戰區網絡作戰控制中心基本上都是被戰區作戰司令部用來對轄區內的全球信息柵格進行指揮控制(轄區內的全球信息柵格也被稱為戰區信息柵格TIG:Theater Information Grid)。
戰區作戰司令部通過戰區網絡作戰控制中心來優化配置和控制全球信息柵格的信息資源,以使它們更好地為戰鬥服務,同時戰區網絡作戰控制中心也是連接國防信息系統局、常規部隊和全球網絡作戰聯合特遣部隊的戰區接口。他們與戰區網絡戰中心、戰區網絡作戰和安全中心合作來監控戰區信息柵格的狀態,對被提議的全球網絡作戰聯合特遣部隊相關行動作出決定,並評估其行動的影響。戰區網絡戰控制中心對作戰行動力度的減小和終止有決定權,並且通過戰區網絡作戰中心和戰區網絡作戰與安全中心來調整作戰的優先級。如果該戰區沒有戰區網絡作戰與安全中心,那麼就由全球網絡作戰與安全中心領帶下的戰區網絡作戰控制中心來負責完成戰區作戰司令部所要求的任務。
美國的北方司令部(NORTHCOM)是一個比較特別的部門,雖然它是一個有著明確防區的戰區作戰司令部,但是其防區內的大部分部隊——包括網絡作戰部隊——都不隸屬於該司令部,而是屬於美國聯合部隊司令部(JFCOM:Join Forces Command)。這樣的部署是為了便於部隊的全球性管理。北方司令部和其他幾個戰區作戰司令部一樣,也設立了戰區網絡作戰控制中心,但是卻沒有建立戰區網絡作戰與安全中心,這就使得北方司令部必須依靠網絡作戰與安全中心等部門為其提供一般支持。在這種情況下,北方司令部所扮演的角色就是需要負責其轄區內的作戰行動,但是又對相應的戰場信息柵格缺乏了解,更沒有直接控制它的權力。
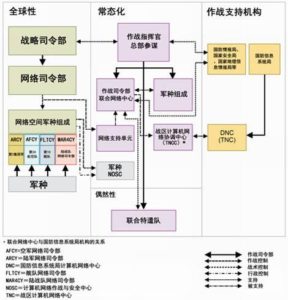
戰略司令部網絡作戰指揮控制
與部隊戰鬥司令部對網絡作戰結構進行調整一樣,國防部的相關部門也在進行著改革。多年以來,國防部一直沒有一個集中控制的網絡作戰部。但是在1997年的時候國防部進行過這方面的嘗試,發現了一些當時網絡的弱點,也得出了“作戰司令部-部隊-國防機構”這種網絡作戰的模式已經不適合現代的戰場情況。那次嘗試促成了國防信息系統局最終組建了一支實體部隊,也就是今天的全球網絡作戰聯合特遣部隊來負責全球信息柵格的操作和防禦。
全球網絡作戰聯合特遣部隊的網絡作戰指揮控制機制同樣也在不斷發展。在現有的聯合司令部計劃(UCP:Unified Command Plan)出現之前,全球網絡作戰聯合特遣部隊的指揮控制都是由戰區作戰司令部負責,但是事實證明這不利於管理網絡中的所有組件,也難以為全球信息柵格提供足夠的事態感知信息。最初版本的網絡作戰的作戰概念比較強調戰區作戰司令部對其防區的網絡作戰的控制,當時對處理戰區問題的描述是這樣的:“作戰司令部有權指揮被指派到其防區的部隊,只要是利於任務的完成,在作戰司令部覺得合適的時候,甚至可以調整全球信息柵格的優先級。所有的這些活動,都應該通過戰區網絡作戰中心來實現。”事實上,即使是全球性的事件,最初版本的網絡作戰概念文件也規定全球網絡作戰聯合特遣部隊需要在戰區作戰司令部的戰區網絡作戰控制中心指揮下進行作戰。
作戰概念的後續版本對這項原則進行了調整。對全球網絡作戰聯合特遣部隊的控制被移到了一個更加全球化的指揮控制架構中,通過這樣的調整,戰略司令部、全球網絡作戰聯合特遣部隊和其他參與網絡作戰的部隊的整體角色都得到了加強。全球網絡作戰聯合特遣部隊的作戰概念被細分成了三個環境作戰概念:全球性的、戰區性的和非全局性的。不同的事件適用何種環境概念取決於事件造成的實際影響和戰區影響。這種形式的指揮控制結構更加適用於目前網絡作戰多樣性特性,針對不同級別的事件,戰區作戰司令部可以採取更加靈活的應對措施,甚至可以同時展開支持性的和輔助性的行動。在這種制度下,有時候處理事件的過程要經過完整的指揮系統鏈,有時候可以跳過一些步驟。
全球性事件
全球性事件是指那些顯而易見會影響整個全球信息柵格的備戰度的活動或事件,這類事件通常需要多個戰區作戰司令部的協同處理才能得到解決。戰略司令部的指揮官必須要具備快速鑑別全球性事件的能力,並要能具體判斷出有哪些戰區作戰司令部或者國防部的其他機構會受到影響。全球性事件包括快速傳播的網絡惡意代碼攻擊、衛星通信攻擊、企業應用攻擊等不僅僅局限於單個戰區的網絡事件。
全球戰略司令部是一個可靠的指揮中心,它對全球網絡作戰聯合特遣部隊和戰區作戰司令部都有命令和指揮權。全球網絡作戰聯合特遣部隊利用自己的資源來執行戰略司令部的指示,作戰命令可以很快地發送到在全球各地的部隊中。值得注意的是,這種命令在傳遞時不經過事件發生地的戰區作戰司令部。
雖然作戰概念的原則賦予了戰略司令部指揮官全球範圍內的指揮權,但是這也並沒有完全否定戰區作戰司令部可以通過分配的聯合司令部計劃來進行指揮的權利。在全球網絡作戰聯合特遣部隊執行戰略司令部的作戰命令的同時,戰區作戰司令部也可以調遣其麾下的部隊進行相應的活動。當然,按照作戰概念的要求,戰區作戰司令部領導下的部隊的行動必須與戰略司令部領導下的全球網絡作戰聯合特遣部隊的行動方針保持一致。事實上,據全球網絡作戰聯合特遣部隊的歷史行動日誌記載,大多數的網絡作戰一開始都是在小範圍戰區開始出現的,戰區作戰司令部總是著手處理這些事件的第一單位,而且如果處理得適當的話,這些戰區級別的事件就不會發展成全球性事件。
戰區性事件
戰區性事件是指那些發生在某個戰場區域,其可預見的影響範圍不會超出該戰區的事件,戰區性事件與全球性事件的最大區別也就在於此。在處理這類事件的時候,戰區作戰司令部起著主導作用,而戰略司令部只承擔輔助的支持作用。全球網絡作戰聯合特遣部隊可以通過其戰區網絡作戰與安全中心對戰區作戰司令部提供支援。如果當地的部隊沒有戰區網絡作戰與安全中心,那也可以通過全球網絡作戰與安全中心為戰區網絡作戰控制中心提供一般支持。戰區作戰司令部對全球網絡作戰聯合特遣部隊的指揮屬於次級指揮,也就是說沒有權利通過全球網絡作戰與安全中心來直接調動全球網絡作戰聯合特遣部隊到其所轄區域進行作戰。
非全局性事件
非全局性事件是指只對職能作戰司令部和特定的國防機構造成影響的事件。由於這類機構沒有明確的防區,所以這些事件既不能被看成全球性的也不能被看成戰區性的。在處理非全局性事件時,戰略司令部扮演輔助指揮的角色,全球網絡作戰聯合特遣部隊對所涉及到的職能作戰司令部提供一般支持。大多數的非全局性事件一般都發生在北方司令部的防區,因為很多相關的職能部門都隸屬於北方司令部。在指揮控制的程序方面,非全局性事件和全球性事件是相同的。
相互矛盾的指揮控制要求
戰術技術的要求
儘管各個部隊的定位不盡相同,但是在網絡作戰中追求高效、合理的作戰方法是他們共同的主題。不同的部隊肩負著不同的職責,他們建立了獨立的作戰網絡、應用設施和輔助工具來滿足自身與全球信息柵格保持聯通的需求。每支部隊都要負責操作一部分全球信息柵格,這在一定程度上需要各部隊間作戰鏈的集中化管理,這樣才能獲得所期待的作戰效率和投入回報率。
關於對全球信息柵格進行集中化控制討論的焦點是網絡作戰的全球性特質。國防部想要實現以網絡為中心的指揮機制、增強部隊的事態感知能力和顯著縮短決策週期的目標的話,唯一的方法就是將網絡和部隊進行橫向的融合,這是一種集中化的控制機制。最新的一份《四年防務評估報告》裡就提到過“要簡化目前的‘煙囪式’系統結構,實現以網絡為中心的指揮機制”。
為了更好地利用緊缺資源,國防部必須從全球性的角度來考慮何時何地調撥何種資源。對衛星傳輸波段、標準戰術入口網絡站點和帶寬等網絡作戰必需資源的分配必須要有明確的任務目標和易於理解的全球性意義。從部隊的角度來看,集中化指揮在某種程度上是對現有部隊機構和作戰、防禦網絡的一次重新洗牌。
由戰區作戰司令部領導的作戰行動將不再嚴格地限於其防區內。地面部隊重新開始利用飛機(包括無人機)例行地在美國本土飛行來支持他們的作戰。隨著快速全球打擊(PGS:Prompt Global Strike)項目的發展,指揮官已經有權力呼叫從戰區以外的武器系統發出常規打擊援助。
在海軍方面,他們指出海上部隊的一個本質性特點就是全球流動性,海軍部隊作戰時會不斷地在各個戰區作戰司令部之間穿插。尤其是像航母戰鬥群這樣的單位,一旦被部署出發,就不可能一直呆在一塊小範圍的戰場。另外,即使是戰區作戰司令部所採取的戰區級別的行動,也有可能產生全球性的影響。網絡防禦姿態的調整可能對互聯網部門帶來巨大的經濟負擔,而且作戰司令部還有可能無法了解到調整行為的具體細節結果。
對國防部的網絡系統來說,所有的攻擊本質上同樣都是全球性的。敵人不可能輕易地從地球的另一端對美國本土的實體目標進行攻擊,但是在計算機網絡科技領域,這樣的事情經常發生。一旦檢測到這種攻擊,關於它的信息必須要在最短的時間內傳遍全球所有的相關部門,以保證從任何地方都能識別出這樣的攻擊方式,從而保護全球信息柵格的安全。每一次網絡入侵——哪怕是看起來無關緊要的失敗的入侵——都有可能給全球信息柵格的內容帶來巨大的潛在危害,因為它們入侵時在系統中留下的後門會在以後的攻擊中發揮作用。病毒的爆發是毫無爭議的全球性事件,如果認識不到這一點的話,我們將會受到更大的損失。
海軍強調沒有任何事件的影響會僅限於某個戰區範圍,所有關於網絡作戰的努力都必須是全球性的。他們的理由是網絡作戰是沒有戰區界限的,國防部的每個戰區作戰司令部所面臨的潛在威脅都是相同的,為了獲得信息上的優勢,國防部必須要充分利用其大覆蓋面的網絡資源,快速地在全球範圍內分享所有的有用信息。
此外,空軍和海軍方面指出,他們的網絡作戰部隊都不是由戰區作戰司令部來負責部署的。在每個戰區作戰司令部的防區內,空軍和海軍都有自己的網絡作戰組織(例如戰區網絡作戰與安全中心),而且空軍和海軍的網絡作戰部隊在戰區內通常是扮演維護者的角色。最後一點,空軍和海軍都認為,根據可供參考的官方文件的描述,戰略司令部通過戰區作戰司令部對全球信息柵格負責。
戰區作戰司令部的要求
對戰區作戰司令部來說,在網絡作戰的指揮控制方面有兩個需要關心的問題。一是需要對戰場信息柵格進行及時的控制,二是需要把網絡變成一個武器系統,讓指揮官們可以像對常規的武器系統一樣共同利用網絡資源,利用網絡全方位的優勢來進行全面的戰鬥。
那些被分配了特定職責的部隊,已經部署好了各自唯一的解決方案,參與到網絡作戰中的每支部隊或者每個機構都相信自己已經擁有了最有效分配緊缺資源的辦法。但是全球信息柵格並不是專屬於某一個部門的,而是一個聯合結構。 “煙囪”式系統和現有的部隊部署方式實際上是降低了戰場信息柵格的利用效率。舉個例子來說,陸軍在國防部的其他部門之前研發出了一套安全的IP電話解決方案,可以進行保密語音的聯絡。出於安全考慮,其他部門通常不會再採用這套方案,而是自己再開發一套功能相同的解決方案。這樣在作戰司令部的防區內就有了兩套獨立的保密IP語音方案,它們相互之間不能進行聯通。戰區作戰司令部只得進行篩選,只保留一套方案,以保證在其防區內所有部門可以進行彼此協作。但是解決方案被淘汰的一方就不能再與該戰區以外的兄弟部隊進行保密聯絡了。
作戰司令部防區內的有些資源可以為多個部隊和公務部門服務。但是也有很多例子是使用者進行重複勞動為各自建立了不能相互聯絡的獨立系統,比如衛星終端和一些技術控制設備。有些時候,要傳遞一個信息的話,需要先把信號發回美國本土,然後再從本土發到距離初始發送者只有兩英里的接收者那裡。各種各樣的光纖一條挨一條地按照相同的路線排列著,但是它們之間的數據卻不能進行直接交換,因為它們分屬於不同的部隊或者公務部門。戰區作戰司令部必須採取措施來解決防區內的部隊或者公務部門之間的互聯性問題。
要解決這個問題,可以採用集中化控制的辦法。對網絡作戰部隊的集中化指揮需要戰區作戰司令部對自身的組織機構進行一定的調整,但是同時又不能影響其在有作戰需要時指揮行動的權力。相關部隊必須接受多個作戰司令部的命令,並且有效地優化和反饋戰場信息。目前,派往前線的部隊獨立性越來越高,通過全球信息柵格的幫助他們可以來回地越過戰區作戰司令部的邊界,戰區作戰司令部對網絡作戰的輔助和對抗作用因此而受到了損害,施行集中化指揮以後,部隊就不能或者說不願意響應戰區作戰司令部的要求了。
在2004年參與印尼海嘯救助工作的時候,太平洋司令部(PACOM:Pacific Command)首次在人道援助行動中採取了“聯合嘗試”的方式。太平洋司令部向被分派有任務的部隊發出指令,讓他們在整個行動計劃的框架之下進行特別的網絡防禦工作。很多海軍部隊和海軍陸戰隊的部隊在海軍全球網絡作戰中心的集中化指揮下,建立了一些相對直接的網絡防禦措施,這些措施超越了太平洋司令部給海軍和海軍陸戰隊分配的任務範圍,這就給太平洋司令部的全球網絡作戰帶來了潛在的危險因素。
作戰司令部很關心總是強調的對全球信息柵格進行集中化控制的思想會降低他們對全球信息柵格的信息掌握度和控制力度。在現有的指揮制度下,一個單位會在其所在部隊的指揮權下進行訓練或者執行其他任務,在戰區作戰司令部的指揮權下參加戰鬥,指揮控制的條理非常清晰。對部隊在信息領域的指揮控制與對其在空中、陸上、海上和空間領域的指揮控制同等重要。對C3S系統(control, communications and computer systems)來說,在其指揮下進行作戰並負責保護它的部隊常常要處於雙重甚至三重的報告鏈中,結果最後分不清到底是誰在負責指揮戰鬥。在全球性或者非全局性事件中,全球網絡作戰聯合特遣部隊經常繞開戰區作戰司令部直接展開行動。儘管聯合網絡作戰的作戰概念專門強調了與戰區作戰司令部進行協調作戰的要求,但是在現代作戰快速變化的環境中,這條要求幾乎成了擺設。信息保障弱點警報系統、計算機任務序列和信息條件調整系統在作戰司令部的轄區之外出現問題就是這條要求失效的典型例子。這些事件直接影響了戰區作戰司令部在戰場上的指揮,當部隊想要直接利用這些機制從管理級上加強自身的控制的時候,他們不能判斷應該在何時、以什麼樣的方式在執行這些操作,也不知道這樣做會對戰區作戰司令部的指揮產生什麼影響,因為在目前的條件下,只有戰區作戰司令部才有能力來進行這些操作。當一個威脅事件需要空軍太空司令部向空軍部隊尋求全球網絡作戰聯合特遣部隊的協同配合的時候,如果不通知或者取得與北方司令部的合作的話,將會給北方司令部的指揮帶來極大的麻煩。
在中央司令部,由於對網絡作戰部隊缺乏足夠的控制,導致指揮官有時候也不能確定網絡資源是否可用。海軍負責操作大量的戰場信息柵格,在作戰區域的海軍網絡作戰部隊並不用對中央司令部的海軍部負責,他們只需要向戰區網絡作戰與安全中心報告。中央司令部的中央戰區戰區網絡作戰中心,其職責是維持和指揮所有戰區作戰司令部的網絡作戰,但是它也不在海軍網絡作戰部隊的報告鏈當中,所以也常常不能獲得所有戰場信息柵格上的事態感知,目前已經有替代辦法來處理這個問題了,不過這還不能說是正式的解決辦法。
對北方司令部來說,因為網絡作戰部隊的控制權的缺乏,他們在2005年“卡特琳娜”颶風的救援工作中遇到了極大的麻煩。在那次行動中,部隊的設備在未經許可的情況下就被運送到了聯合作戰區域。這使得北方司令部無法掌握和引導物資的調動情況,更無法協同各個部隊的行動,這是個多方位的管理和操作問題。
在各個部隊都主張施行在以全球網絡作戰聯合特遣部隊為中心的集中化指揮構架的時候,我們有必要強調一個事實,那就是戰區司令部並不願意看到這樣的變化,他們想保持原有的他們對戰略司令部負責,擁有全球信息柵格的操作權和防禦權的機制。戰略司令部的存在對保持戰區作戰司令部在戰區和全球性事件的作戰行動中的指揮地位以及增強戰區作戰司令部與聯合參謀部的溝通都有很大的幫助。
作戰司令部和部隊方面都想從聯合作戰的層面上對網絡作戰進行集中化指揮,但是其中有幾個問題還需要討論:
1.誰負第一領導責任?
2.網絡作戰進行集中化指揮具體在哪個層面上得到體現,全球層面、戰區層面還是其他什麼層面?
3.這種調整帶來的改變是僅僅體現在戰區作戰司令部的某個部門向全球網絡作戰聯合特遣部隊發出請求時還是戰區作戰司令部獲得戰區內的完全指揮權和優先權?
最後,戰區作戰司令部是最終對總統負責的以完成轄區內的軍事任務為目標的機構,被派遣到戰區作戰司令部的部隊需要在其管轄權之下完成各自的任務。因此在部隊方面主張實施全球性的集中指揮的時候,他們仍然會處於戰略司令部的指揮之下這一點是不容置疑的。但是目前全球信息柵格是影響戰區作戰司令部的指揮控制能力和指揮官對部隊的指導能力的關鍵一環。沒有全球信息柵格的話,飛機不能飛行、地面部隊無法移動、艦艇不能航行,連衛星都不能提供信號。指揮官們需要獲取全球信息柵格的狀態並進行控制,就像他們需要掌握部隊的方位和狀態一樣重要。他們必須要掌握戰場信息柵格的範圍、能力和狀態,必須知道戰區以外的情況會如何影響部隊所在區域的戰場信息柵格,還必須能夠指揮和優化部隊配置以支持作戰。如果我們真的相信被描述得天花亂墜的集中化指揮會有更好的效果,那也不能忽視為戰區作戰司令部保留適當的指揮和控制權。
還有,只要戰區作戰司令部這種結構還保留著,那麼所有的軍事任務,包括那些由職能作戰司令部指揮的作戰,都必然還是會發生在戰區作戰司令部的防區內,因為所有的網絡作戰任務都必定要由一個實體單位來執行。同時,集中化指揮對於實現以網絡為中心的指揮模式以及更加有效地防禦攻擊、傳遞信息都是必要的。這種集中化指揮的概念與戰區作戰司令部要求掌握和優化戰場信息柵格的願望是不互斥的。
前進之路
要想制定出一套可行的網絡作戰指揮控制框架,必須要避免走極端,既要考慮戰區作戰司令部的需要,也要考慮建立對全球信息柵格的集中化控制的需要。在目前聯合網絡作戰的作戰概念的發展過程和網絡作戰部隊的轉型過程中,組織原則需要發揮調整各方利益的槓桿作用。為了達到這樣的目標,國防部應該做到以下幾點:
1.創建一個簡單、明確的網絡作戰指揮鏈,保證戰略司令部可以對所有的網絡作戰行動進行指揮。這就可以解決剛才提到的“誰負第一領導責任”的問題。只有當事件發生在快速變化的環境中的時候,戰區指揮控制機構才開始發揮作用。簡潔的指揮鏈可以保證參加網絡作戰的部隊知道自己應該聽從誰的指揮、應該向誰報告,在這條指揮鏈中,必須包括戰區作戰司令部。
2.可以賦予戰區作戰司令部在其防區內的指揮權:
——修正聯合司令部計劃以明確戰區作戰司令部在其防區內對網絡作戰的職責。
——修正已有的全球信息柵格網絡作戰概念,詳細說明那些處在戰區網絡作戰與安全中心之外的部隊可以從戰區作戰司令部的全球網絡作戰與安全中心獲得直接援助。
——規定全球網絡作戰聯合特遣部隊的所有命令都要通過戰區作戰司令部來執行。
這些調整可以保證戰區中的所有單位都在唯一的一條指揮鏈下行動,那就是通過戰區作戰司令部對戰略司令部負責。這也可以解決北方司令部應該對轄區負責但是又沒有指揮網絡作戰的權力的尷尬境地。
3.在每個戰區作戰司令部建立一個由中央司令部管轄的聯合網絡作戰中心,將戰區作戰司令部的戰區網絡作戰控制中心和全球網絡作戰聯合特遣部隊的戰區網絡作戰中心進行融合。這樣一來,每個戰區作戰司令部都將有一個在計算機空間領域的聯合作戰司令部,就像在海陸空的實體戰場上一樣。任何處在戰區網絡作戰與安全中心之外的部隊都可以從聯合網絡作戰中心的全球網絡作戰與安全中心獲得直接援助。
4.鞏固全球信息柵格的地位,將最高控制權交給戰略司令部。目前集中化指揮的發展偏重於對參與網絡作戰的部隊的指揮,這與以網絡為中心的指揮概念背道而馳。以部隊為中心的“煙囪”式指揮系統不利於信息的傳遞和處理,讓我們離“為所有使用者提供最新、最準確的信息”的目標越來越遠。在之前的《戈德華特·尼科爾斯國防部重構法》報告中已經明確提到,組織管理和指揮控制應該由一個聯合的機構來掌控。
結束語
目前對網絡作戰的集中化指揮是一個迫切的需要。優化網絡作戰指揮機制可以幫助國防部提高效率、節約成本以及更好地分配緊缺資源。更重要的是,這樣可以讓網絡作戰部隊更加快速、準確地為指揮官提供信息,這在大規模的網絡作戰中非常重要。集中化指揮的進程不能影響到網絡作戰指揮控制的效率。這取決於全球信息柵格能否為所有參戰的單位提供足夠的信息以及指揮官是否充分利用戰區信息柵格來幫助指揮作戰。
“我們必須改變對網絡作戰問題的討論和思考模式,我們是在進行網絡“作戰”而不是網絡“管理”,所有的參戰單位必須保證自己每時每刻都準備著開戰,以保證網絡系統這一決定性的武器系統的安全”。網絡作戰是我們國家能夠贏得戰爭的關鍵一環,它可以幫助我們提供指揮和控制、縮短決策週期以及調整各戰區的資源配備。戰略司令部已經在強化網絡作戰概念方面邁出了很大的一步,這些努力還需要繼續進行下去。戰區作戰司令部必須是掌控和防護全球信息柵格的重要一環,以保證我們可以繼續取得網絡作戰的勝利。
Reference URL: http://www.china.com.cn/military