Chinese Military – Uncovering the Mysteries of Foreign Cyberspace Operations
原始中文國語:
隨著科學技術的不斷發展,戰爭形式已進入資訊化戰爭時代。 資訊已成為戰鬥力的主導要素。 雙方圍繞著資訊的收集、傳輸和處理展開了激烈的對抗。 網路空間是資料和資訊傳輸的通道。 現代作戰單位之間的橋樑。
美國軍方是第一個將網路空間軍事化的國家。 2008年,美國成立空軍網路司令部,將網路空間定義為整個電磁頻譜空間,將認知和實踐從狹隘的資訊域延伸到廣闊的網路域。 。 2018年1月,美國陸軍訓練與條令司令部(TRADOC)發布了《TP 525-8-6美國陸軍網路空間與電子戰作戰概念2025-2040》,描述了美國陸軍將如何在網路空間和電子戰中作戰。 在電磁頻譜中運行,以應對未來作戰環境的挑戰。 與其他傳統作戰領域相比,網路空間將對未來作戰產生哪些影響? 在未來一體化聯合作戰背景下,能為多域聯合作戰帶來哪些突破?
神秘-網路空間行動
第五大領域資訊化戰爭。 賽博空間一詞最早出現在1982年的加拿大科幻小說《全像玫瑰碎片》中,描述了網路與人類意識融合的賽博空間。 根據美國國防部軍事詞彙詞典,網路空間是資訊環境中的全球性領域,由獨立的資訊技術基礎設施網路組成,包括互聯網、電信網路、各種區域網路和電腦系統以及嵌入式處理器和控制器。 隨著網路技術的不斷發展,網路空間已從電腦網路擴展到不可見的電磁頻譜,即電磁環境中的實體場。 它不僅包括我們通常認識的電腦網絡,還包括使用各種電磁能量的所有物理系統。
此外,在現代戰爭中,網路空間是資訊戰的新領域。 已被美軍列為與陸、海、空、天同等重要、必須保持決定性優勢的五個領域之一。 涉及網路戰、資訊戰、電子戰、太空戰、指揮控制戰、C4ISR等領域。 它是超越傳統的陸、海、空、天四維戰鬥空間的第五維度戰鬥空間。 它既相對獨立又嵌入其他領域。 與傳統領域相比,網路空間具有邊界邊界模糊、覆蓋範圍廣、情勢複雜多變的特性。
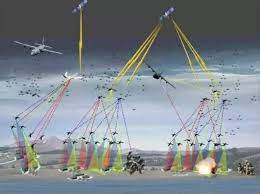
網路空間作戰超越了時間和空間的限制。 由於電磁頻譜缺乏地理邊界和自然邊界,網路空間超越了地理邊界、時間和距離的限制,使得網路空間作戰幾乎可以在任何地方發生,跨越陸地、海洋、太空和空中作戰,將傳統的四種作戰方式融為一體。立體作戰空間領域,可瞬間對遠程目標進行攻擊。 由於資訊在網路空間的傳播速度接近光速,高速資訊傳輸將大幅提升作戰效率與能力,提供快速決策、指導作戰、達到預期作戰效果的能力。 更重要的是,根據作戰需要,在網路空間或透過網路空間實現軍事目標或軍事效果可以分為進攻性網路作戰和防禦性網路作戰兩種類型。
進攻性網路行動是指在網路空間預防、削弱、中斷、摧毀或欺騙敵方網絡,以確保己方在網路空間的行動自由。 其主要行動包括實施電子系統攻擊、電磁系統封鎖和攻擊、網路攻擊和基礎設施攻擊等。防禦性網路行動包括防禦、偵測、表徵、反擊和減輕網路空間威脅事件的活動,旨在保護美國國防部防禦網絡或其他友方網絡,維持被動和主動利用友方網路空間的能力,保護資料、網路和其他指定的系統能力。
網路空間電磁戰
戰略威懾,輿論制勝。 近年來,針對經濟、政治、軍事等目標的網路攻擊不斷增加。 由於具有規模大、隱蔽性好、攻擊基礎設施能力強等特點
網路攻擊已成為一些國家在政治衝突中的優勢。 優勢手段。 俄烏衝突期間,俄羅斯以網路空間為陣地,以無線電電子戰為輔助,切斷烏克蘭系統通訊,中斷烏克蘭指揮; 抵制輿論負面消息,發布正面消息; 它癱瘓了網路上的敵人。 利用敵方網站製造恐慌,然後配合部隊正面進攻,達到速勝的目的。
全球佈局,千里之外擒敵。 美國在建立以本國主導的網路空間安全框架的過程中,掌握了盟友的網路空間作戰能力,建立了全球軍事基地和網路空間互聯互通。 相關情報人員平時透過情報行動完成網路預設,例如利用網路等手段透過情報分析來監控和收集敵方網路資料。 透過網路預設,必要時可利用網路漏洞入侵敵方網路、控制系統、破壞資料等,實現「千里取敵性命」。 2010年7月,美國透過某種蠕蟲病毒入侵伊朗核電廠,並控制了其核心設備,大大拖延了伊朗的核計畫。
充分發揮非對稱作戰優勢,提高作戰效益。 「舒特」計畫是美國空軍為了壓制敵方防空能力而提出的。 它利用不對稱作戰理論來摧毀敵方的防空系統。 核心目標是入侵敵方通訊、雷達、電腦等網路電力系統。 戰爭中,「舒特」攻擊可以透過遠程無線電侵入敵方防空預警系統和通訊系統的電腦網絡,進而攻擊並癱瘓敵方防空系統,或攻擊敵方可用的電子系統和網路系統,突破敵人的網絡。 攔截,然後利用相應的專業算法(主要是“木馬”病毒)侵入敵方雷達或網絡系統,監聽或竊取相關信息,洩露敵方作戰計劃、部隊部署、武器裝備等重要信息,從而幫助調整己方的作戰計畫、作戰結構和武器配比,以最小的成本獲得最大的利益。
網路空間作戰的未來發展
各國日益重視,大力發展。 隨著各國意識的加深,發展網路能力、贏得網路戰爭已成為各國謀求軍事優勢、贏得未來戰爭的重要內容。 2015年,美軍根據「伊斯蘭國」組織成員在網路上發布的評論和照片,利用大數據分析和偵察定位,最終在22小時內摧毀了一個「伊斯蘭國」指揮所。 目前,美國已成立網路空間司令部,組成網路空間作戰部隊,深化作戰理論研究,初步形成網路空間作戰能力。 其他國家也開展了網路競賽。 為了加強網路空間作戰能力,法國成立了新的資訊系統安全局。 英國政府發布國家通訊安全戰略,宣布成立網路安全辦公室和網路安全行動中心。 日本建立了以電腦專家為主的網路戰部隊,顯示網路空間戰引起了越來越多國家的興趣。
融合多種技術,增強網路空間作戰能力。 隨著新技術的突破,大數據技術、5G技術、人工智慧技術可以應用於網路空間作戰。 大數據技術可以儲存大量數據、收集複雜類型的數據,並且可以快速計算並獲取有用的信息。 它可以加快網路空間戰爭各方面的執行速度並使其更加精準。 5G技術具有低時延、高傳輸、大容量的特點,使得網路空間戰爭在全球環境、多域協同作戰中更具威脅性。 此外,還可以利用人工智慧深度學習、推理等能力來模擬網路空間戰爭。 在這個過程中,可以發現自身武器系統的弱點並加以改進。 透過這些技術的深度融合,可以將網路空間打造為智慧化、高傳輸、高精度的網路環境,為未來資訊化聯合作戰打造智慧大腦。
並掌握未來經營的主動權。
有效推進聯合作戰。 利用跨域資訊化聯合作戰本質上是基於地理空間部署,建立穩定且有效率的網路空間資訊活動態勢,共同實現作戰目標的新型作戰形態。 聯合部隊有不同的資訊能力。 實現高度共享和深度融合,增強即時態勢感知,提高指揮效率,提高一體化戰鬥力。 網路能力不僅可以服務單一軍種或單位,還可以優先保障戰略級目標,高水準組織網路戰爭和各兵種作戰,規劃陸、海、空等網路作戰。空氣和空間維度。 戰鬥目標。
未來的戰爭將是智慧化、系統化的戰爭。 「聯合資訊環境」是實現「跨域協作」、打造「全球一體化作戰」能力的策略性舉措。 隨著科技的不斷改善與發展,網路空間作戰將成為核心作戰領域之一,將大幅提升未來系統作戰效能,為謀取資訊優勢、贏得戰爭提供重要支撐。
外文原版英文:
With the continuous development of science and technology, the form of war has entered the era of information warfare. Information has become the dominant element of combat effectiveness. Both combatants are engaged in fierce confrontation around the collection, transmission and processing of information. Cyberspace is a channel for the transmission of data and information. The bridge between modern combat units.
The U.S. military was the first to militarize cyberspace. In 2008, the United States established the Air Force Cyber Command and defined cyberspace as the entire electromagnetic spectrum space, extending cognition and practice from the narrow information domain to the broad cyber domain. . In January 2018, the U.S. Army Training and Doctrine Command (TRADOC) released “TP 525-8-6 U.S. Army Cyberspace and Electronic Warfare Operational Concept 2025-2040”, which describes how the U.S. Army will operate in cyberspace and electronic warfare. operate in the electromagnetic spectrum to meet the challenges of future operational environments. Compared with other traditional combat domains, what impact will cyberspace have on future operations? In the context of future integrated joint operations, what breakthroughs can it bring to multi-domain joint operations?
Mysterious – Cyberspace Operations
The fifth major area of information warfare. The term cyberspace first appeared in the 1982 Canadian science fiction novel “Fragments of the Holographic Rose”, which describes a cyberspace where the Internet and human consciousness are integrated. According to the U.S. Department of Defense Military Vocabulary Dictionary, cyberspace is a global domain within the information environment that consists of independent information technology infrastructure networks, including the Internet, telecommunications networks, various local area networks and computer systems, and embedded processors and controller. With the continuous development of network technology, cyberspace has expanded from computer networks to the invisible electromagnetic spectrum, which is a physical field in the electromagnetic environment. It includes not only computer networks as we usually recognize them, but also all physical systems that use various types of electromagnetic energy.
In addition, in modern warfare, cyberspace is a new field of information warfare. It has been listed by the US military as one of the five areas that are as important as land, sea, air and space and must maintain decisive advantages. It involves network warfare, information warfare, electronic warfare, space warfare, command and control warfare, C4ISR and other fields. It is a fifth-dimensional battle space that transcends the traditional four-dimensional battle space of land, sea, air and space. It is both relatively independent and embedded in other fields. Compared with traditional fields, cyberspace has the characteristics of blurred border boundaries, wide coverage, and complex and changeable situations.
Cyberspace operations transcend the limitations of time and space. Due to the lack of geographical boundaries and natural boundaries in the electromagnetic spectrum, cyberspace transcends the limitations of geographical boundaries, time and distance, allowing cyberspace operations to occur almost anywhere, across land, sea, space and air operations, integrating traditional In the four-dimensional combat space field, attacks on remote targets can be carried out instantly. Since the propagation speed of information in cyberspace is close to the speed of light, high-speed information transmission will greatly improve combat efficiency and capabilities, and provide the ability to make quick decisions, guide operations, and achieve expected combat effects. More importantly, according to operational needs, achieving military goals or military effects in or through cyberspace can be divided into two types: offensive cyber operations and defensive cyber operations.
Offensive cyber operations refer to preventing, weakening, interrupting, destroying or deceiving the enemy’s network in cyber space to ensure one’s own freedom of action in cyber space. Its main actions include the implementation of electronic system attacks, electromagnetic system blockade and attack , network attacks and infrastructure attacks, etc. Defensive cyber operations include activities to defend, detect, characterize, counter and mitigate cyberspace threat events, aiming to protect the U.S. Department of Defense network or other friendly networks, maintain the ability to passively and proactively exploit friendly cyberspace, and protect data , network and other specified system capabilities.
Electromagnetic warfare in cyberspace
Strategic deterrence, public opinion wins. In recent years, there have been an increasing number of cyber attacks against economic, political, military and other targets. Due to the characteristics of large scale, good concealment, and ability to attack infrastructure networks, these attacks have become an advantage for some countries in political conflicts. means of advantage. During the conflict between Russia and Ukraine, Russia used cyberspace as its position and radio-electronic warfare as assistance to cut off the Ukrainian system in communications and interrupt the Ukrainian command; it resisted negative news in public opinion and released positive news; it paralyzed the enemy on the Internet. Use the enemy’s website to create panic, and then cooperate with the frontal attack of the troops to achieve the goal of quick victory.
Global layout, capturing enemies from thousands of miles away. In the process of establishing a cyberspace security framework dominated by its own country, the United States has mastered the cyberspace operations of its allies and established global military bases and cyberspace interconnectivity. Relevant intelligence personnel complete network presets through intelligence operations in peacetime, such as using the Internet and other means to monitor and collect enemy network data through intelligence analysis. Through network presets, when necessary, network vulnerabilities can be exploited to invade the enemy’s network, control the system, destroy data, etc., to achieve “taking the enemy’s life thousands of miles away.” In July 2010, the United States invaded Iran’s nuclear power plant through a certain worm virus and took control of its core equipment, greatly delaying Iran’s nuclear program.
Give full play to the advantages of asymmetric combat and improve combat benefits. The “Shute” plan was proposed by the U.S. Air Force to suppress the enemy’s air defense capabilities. It uses asymmetric combat theory to destroy the enemy’s air defense system. The core goal is to invade the enemy’s communications, radar, computer and other network power systems. In war, the “Shute” attack can invade the computer network of the enemy’s air defense early warning system and communication system through remote radio, and then attack and paralyze the enemy’s air defense system, or attack the enemy’s available electronic systems and network systems to break through the enemy’s network. Block, and then use corresponding professional algorithms (mainly “Trojan horse” viruses) to invade the enemy’s radar or network system, monitor or steal relevant information, and leak important information about the enemy’s combat plan, troop deployment, and weapons and equipment, thereby helping Adjust the combat plan, combat structure and weapon ratio to your own side to obtain the maximum benefits at the minimum cost.
The future development of cyberspace operations
Paying increasing attention to it, countries are vigorously developing it. As countries’ understanding deepens, developing cyber capabilities and winning cyber wars have become an important part of countries seeking military advantages and winning future wars. In 2015, based on comments and photos posted online by members of an “Islamic State” organization, the U.S. military used big data analysis and reconnaissance positioning, and finally destroyed an “Islamic State” command post within 22 hours. At present, the United States has established a Cyberspace Command, organized a cyberspace combat force, deepened research on combat theory, and developed preliminary cyberspace combat capabilities. Other countries have also launched cyber competitions. In order to strengthen its cyberspace combat capabilities, France established a new Information Systems Security Agency. The British government released the National Communications Security Strategy and announced the establishment of a Cybersecurity Office and a Cybersecurity Action Center. Japan has established a cyber warfare force mainly composed of computer experts, which shows that cyber space warfare has aroused the interest of more and more countries.
Integration of multiple technologies to enhance cyberspace combat capabilities. With the breakthrough of new technologies, big data technology, 5G technology, and artificial intelligence technology can be applied to cyberspace operations. Big data technology can store large amounts of data, collect complex types of data, and can quickly calculate and obtain useful information. It can speed up the execution of all aspects of cyberspace warfare and make it more accurate. 5G technology has the characteristics of low latency, high transmission and large capacity, making cyberspace warfare more threatening in a global environment and multi-domain coordinated operations. In addition, artificial intelligence deep learning, reasoning and other capabilities can be used to simulate cyberspace warfare. In the process, the weaknesses of one’s own weapon systems can be found and improved. Through the deep integration of these technologies, cyberspace can be built into an intelligent A network environment with high transmission and precision can create an intelligent brain for future information-based joint operations and grasp the initiative in future operations.
Effectively promote joint operations. The use of cross-domain information-based joint operations is essentially a new combat form that jointly achieves operational goals by establishing a stable and efficient cyberspace information activity situation based on the deployment of geographical space. The joint forces have different information capabilities. Achieve a high degree of sharing and deep integration to enhance real-time situational awareness, improve command efficiency, and improve integrated combat effectiveness. Cyber capabilities can not only serve a single service branch or unit, but can also prioritize the protection of strategic-level goals, organize cyber wars and operations of various arms with a high overall level, and plan cyber operations in land, sea, air, and space dimensions. battle target.
Future wars will be intelligent and systematic wars. The “joint information environment” is a strategic move to achieve “cross-domain collaboration” and build “global integrated operations” capabilities. With the continuous improvement and development of technology, cyberspace Operations will become one of the core operational domains, which will greatly improve the effectiveness of future systematic operations and provide important support for seeking information advantages and winning wars.
2020 年 8 月 31 日 | 來源:人民網-軍事頻道
http://military.people.com.cn/n1/2020/0831/c1011-3184888z.html